Explanation
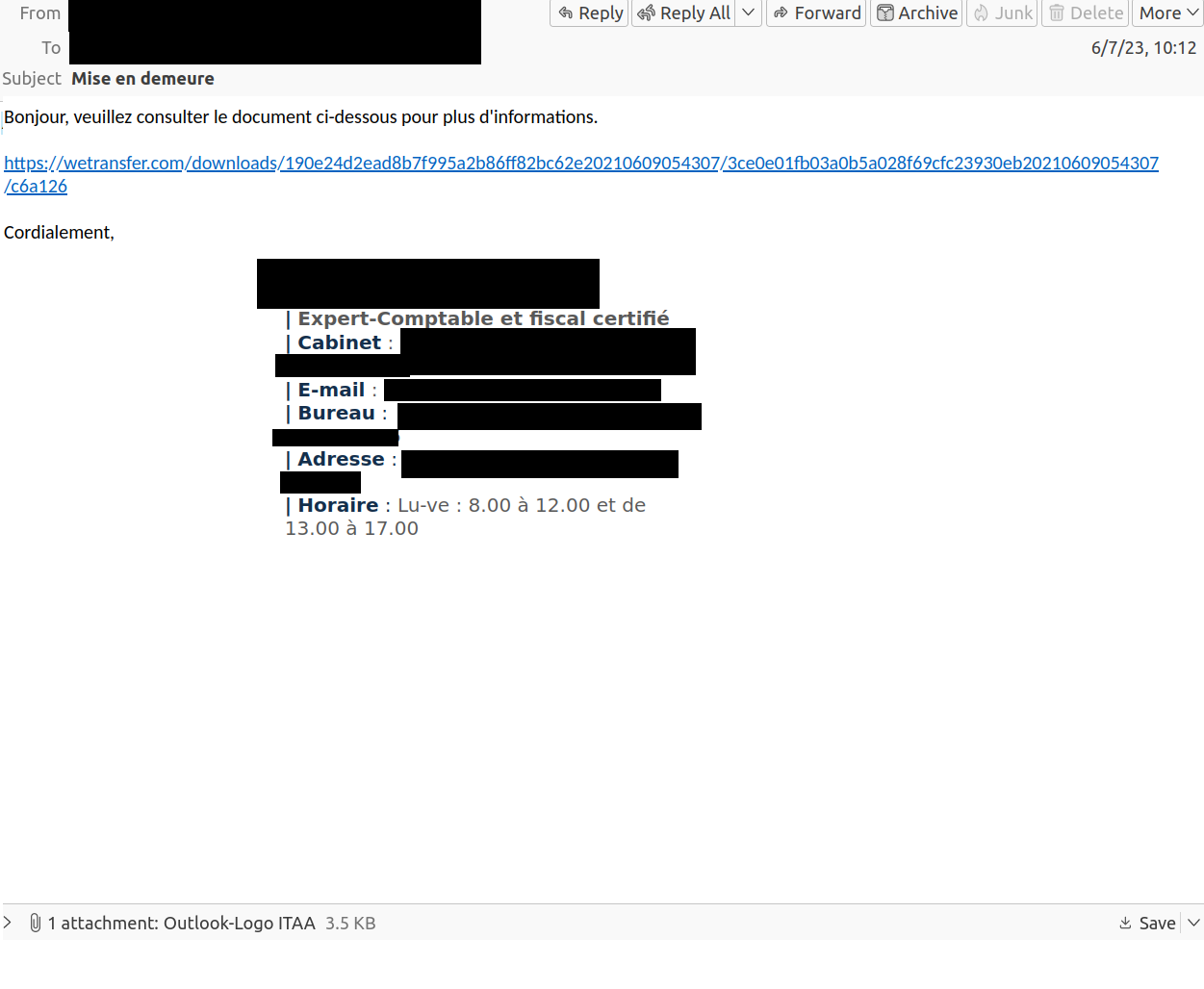
Threat actors are using compromised accounts to collect e-mail credentials. By using compromised accounts, the e-mail seems legitimate at first glance as it seems to originate from a known and trusted source. In reality, however, it is malicious.
The phishing mail leads the user to believe that there is a notice of default with a document containing more information.
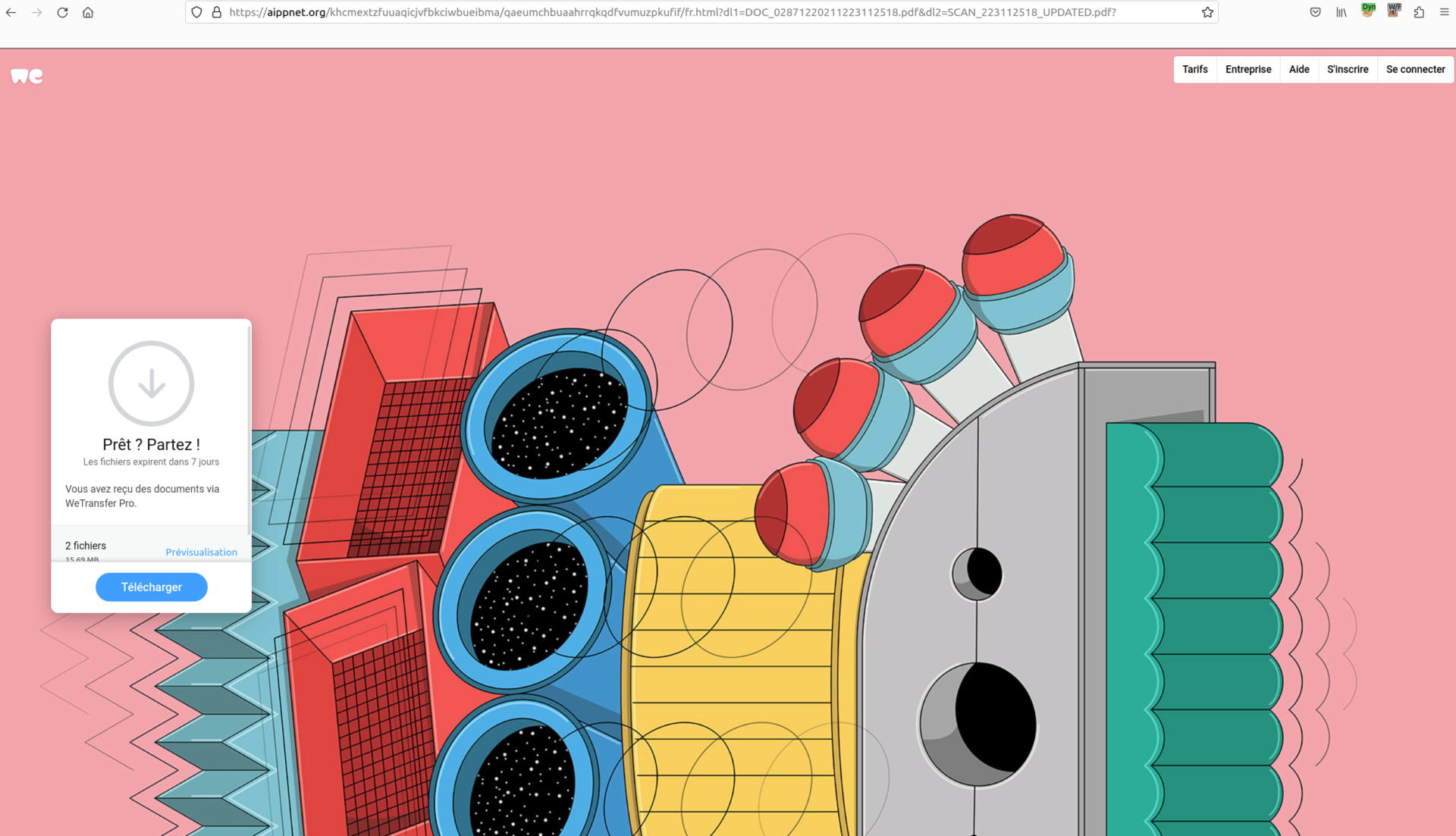
By clicking on the fake wetransfer link the user is redirected to a fake wetransfer landing page.
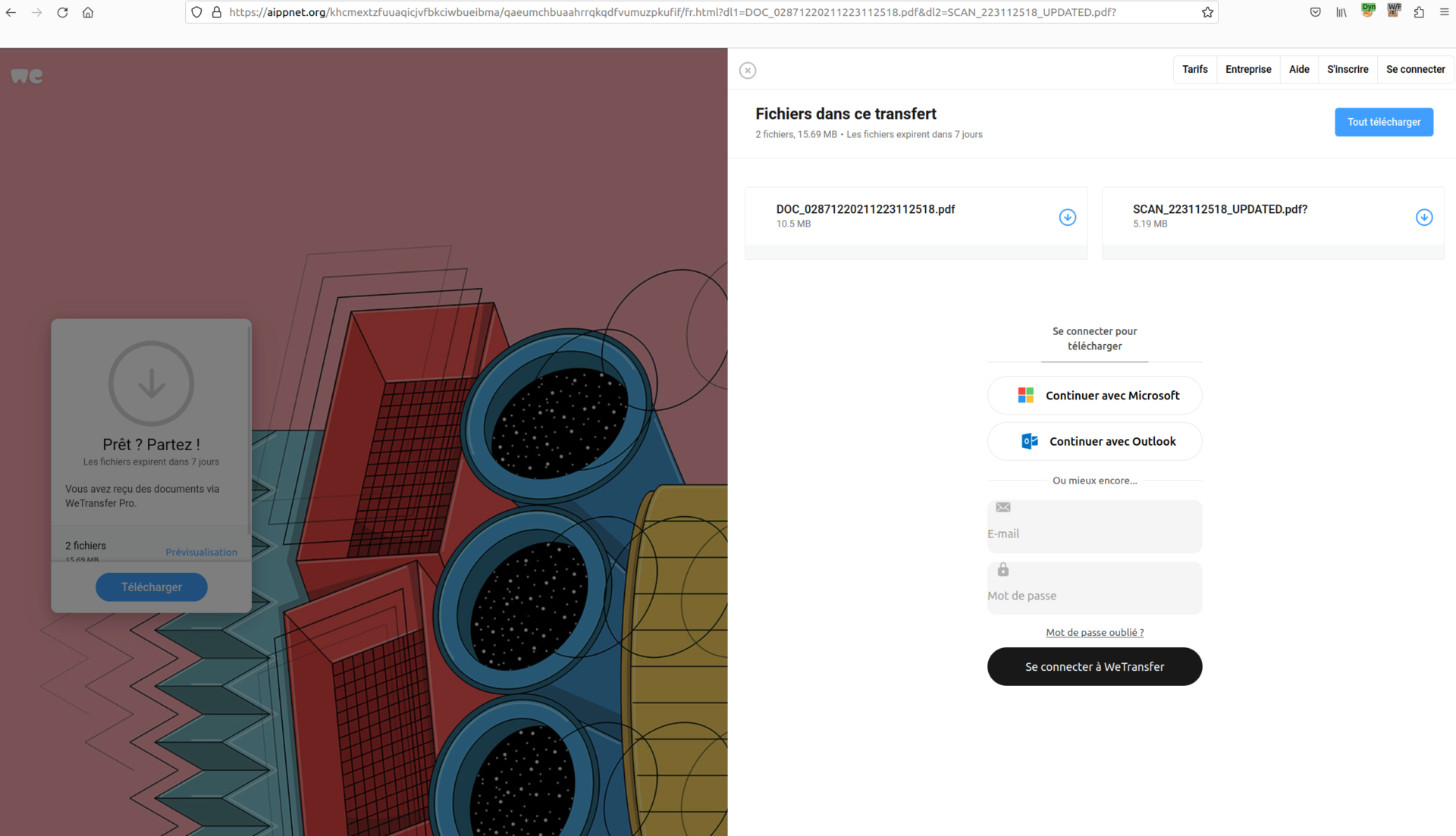
Clicking on ‘Télécharger’ shows the phishing form, which asks for e-mail credentials.
Example