Explanation
Threat actors are using compromised accounts to collect Microsoft e-mail credentials. By using compromised accounts, the e-mail seems legitimate at first glance as it seems to originate from a known and trusted source. In reality, however, it is malicious.
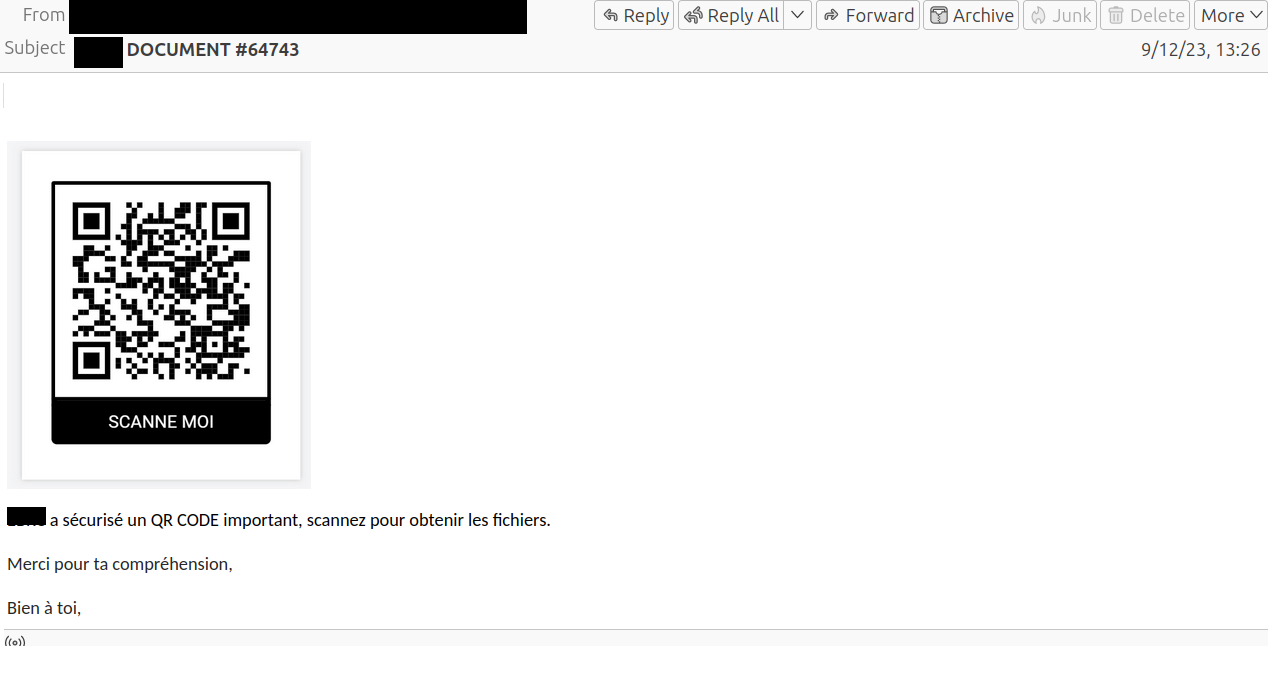
The phishing mail leads the user to believe that important files have been sent.
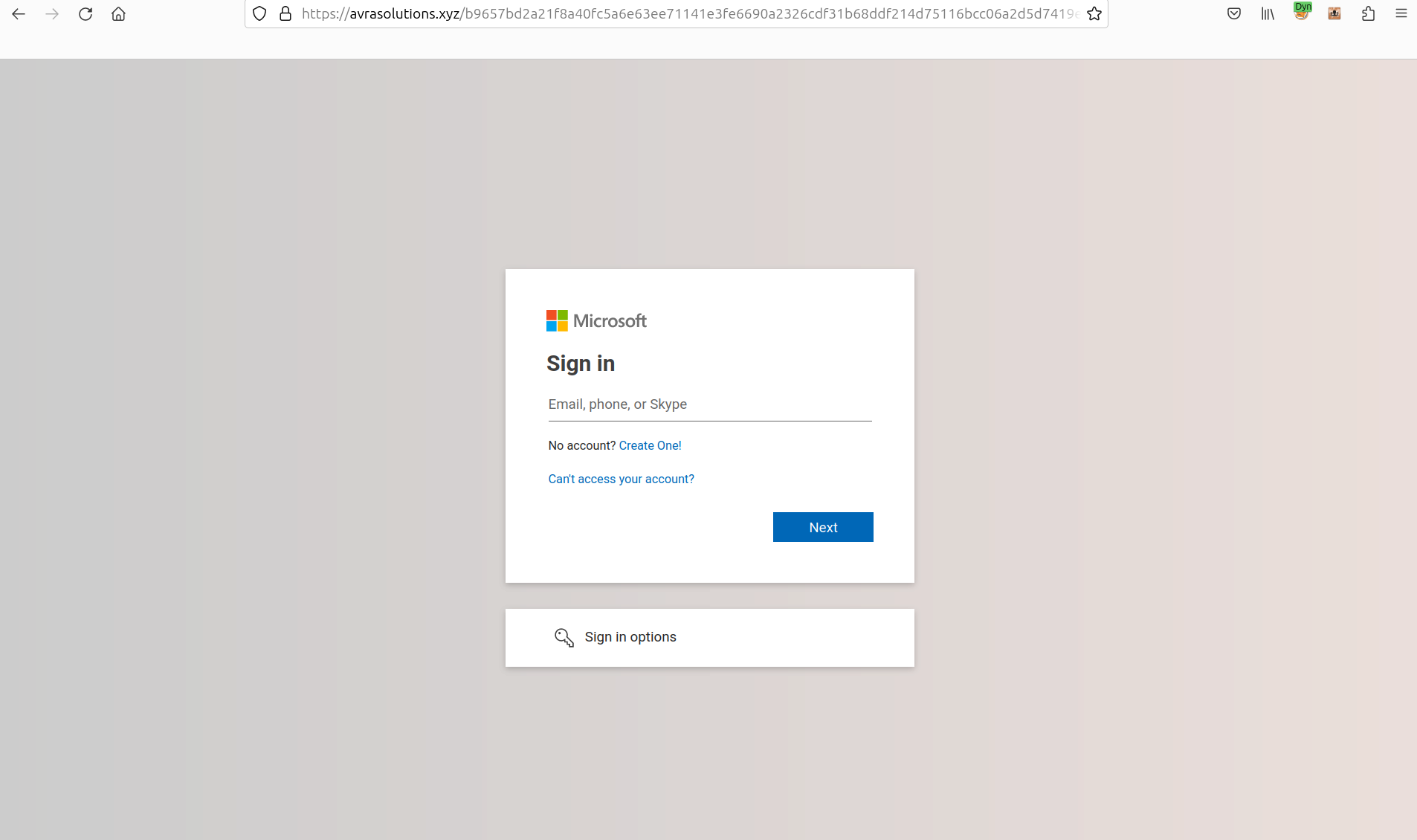
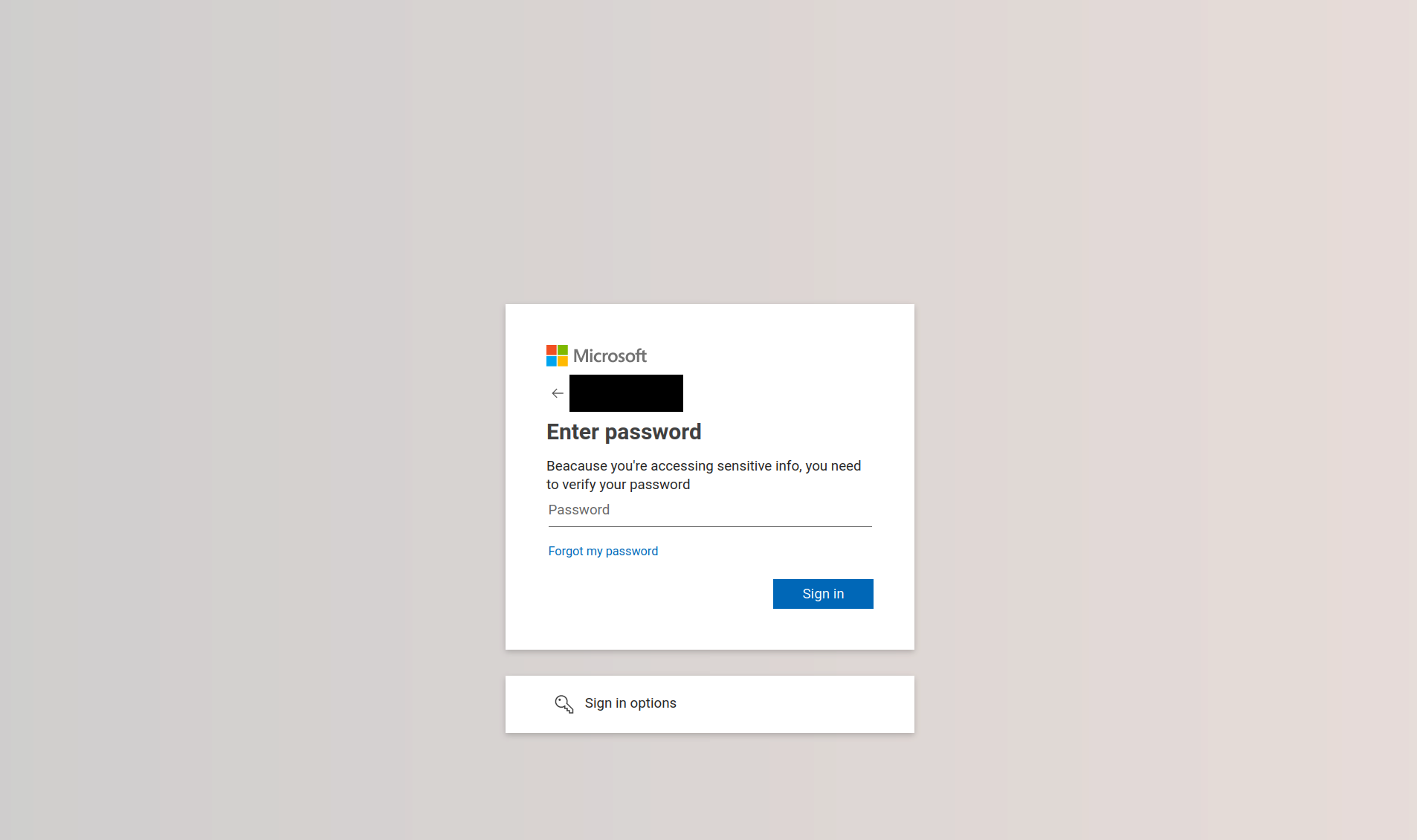
By scanning the QR code in the e-mail the user is redirected to a fake Microsoft login page, where they are asked for their username and password.
Example