Explanation
Threat actors are using compromised accounts of a hotel to collect Microsoft e-mail credentials. By using compromised accounts, the e-mail seems legitimate at first glance as it seems to originate from a known and trusted source. In reality, however, it is malicious.
The phishing mail leads the user to believe that a proposition regarding a hotel reservation is to reviewed.
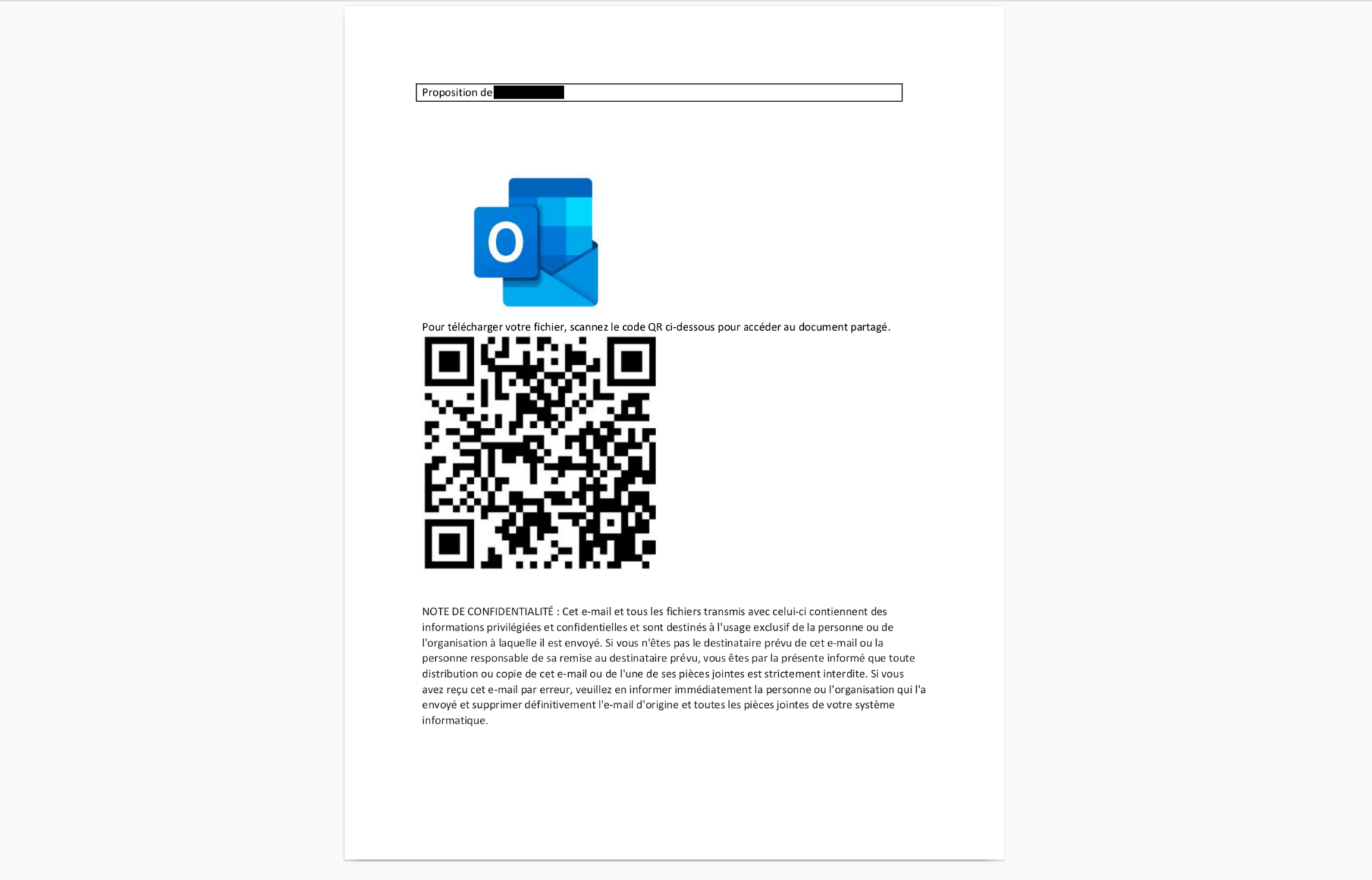
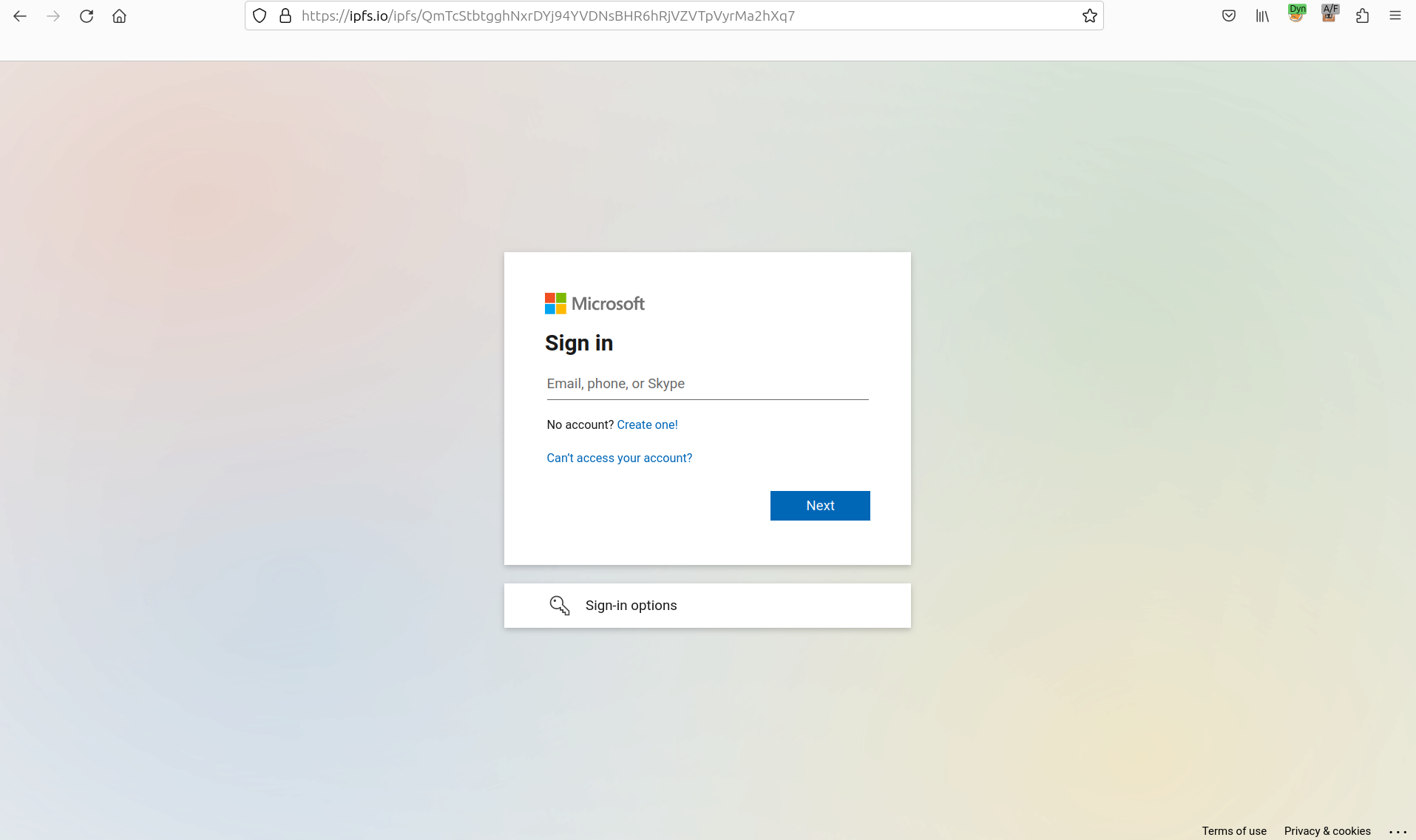
By opening the attachment and scanning the QR code the user is redirected to a fake Microsoft login page, where they are asked for their username and password.
Example