Explanation
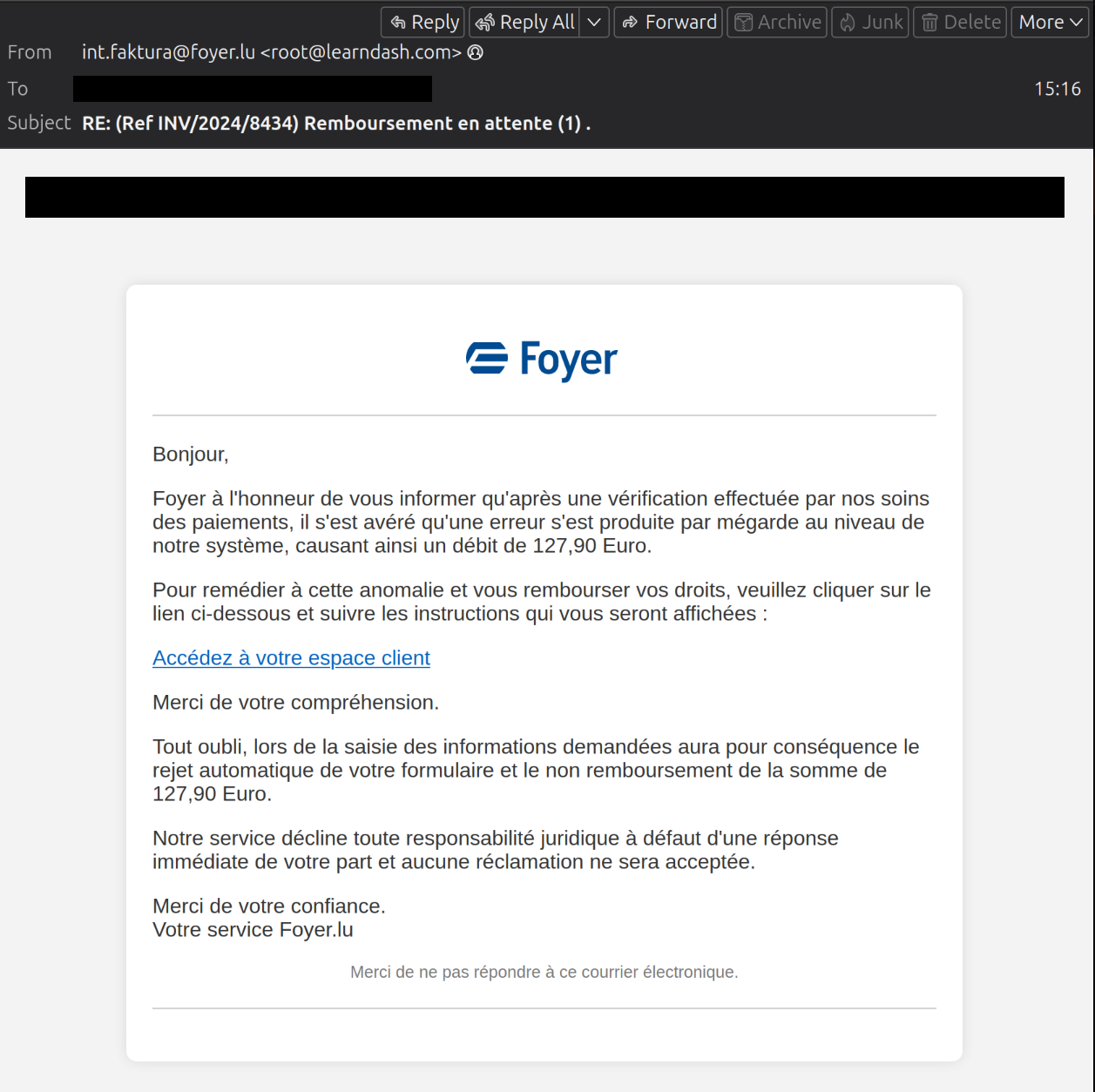
This phishing involves collecting LuxTrust and credit card credentials by impersonating Foyer. The e-mail claims that a mistake has been made and that you should click on the link to get the money back.
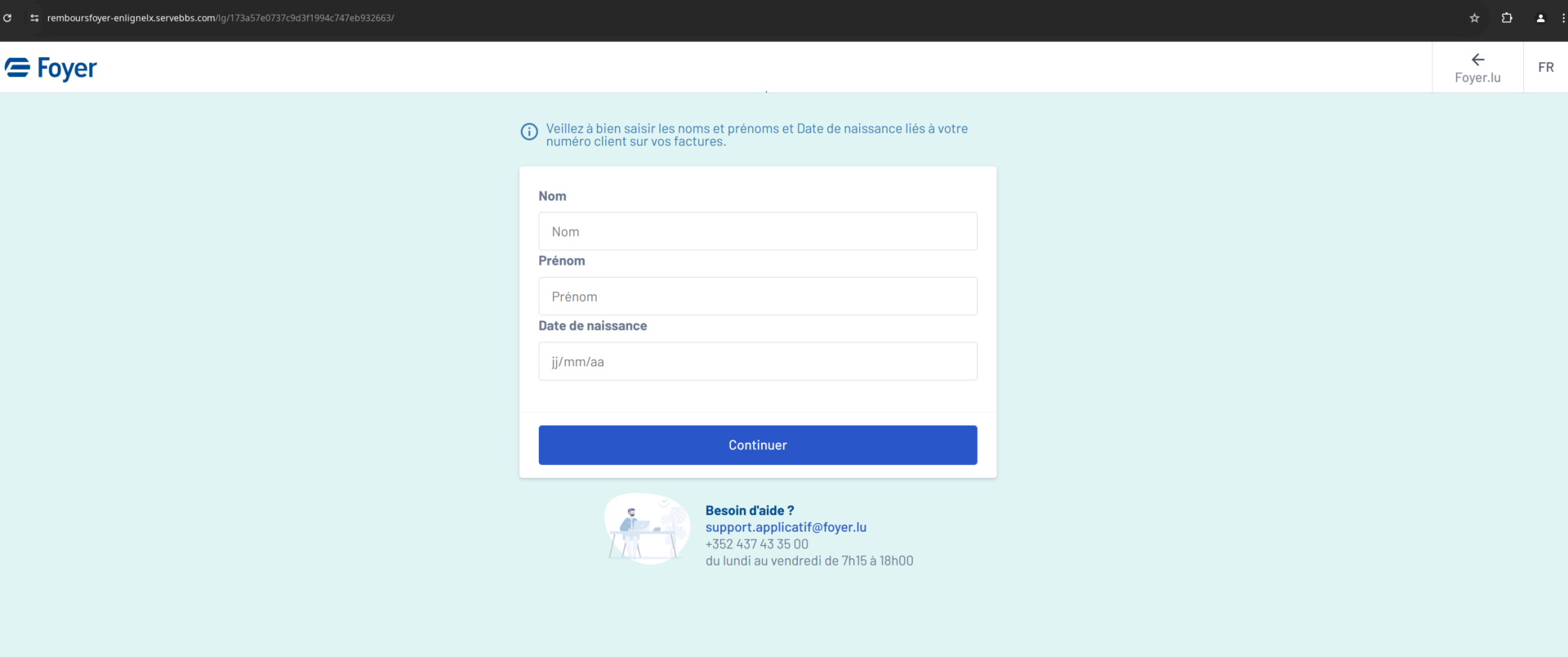
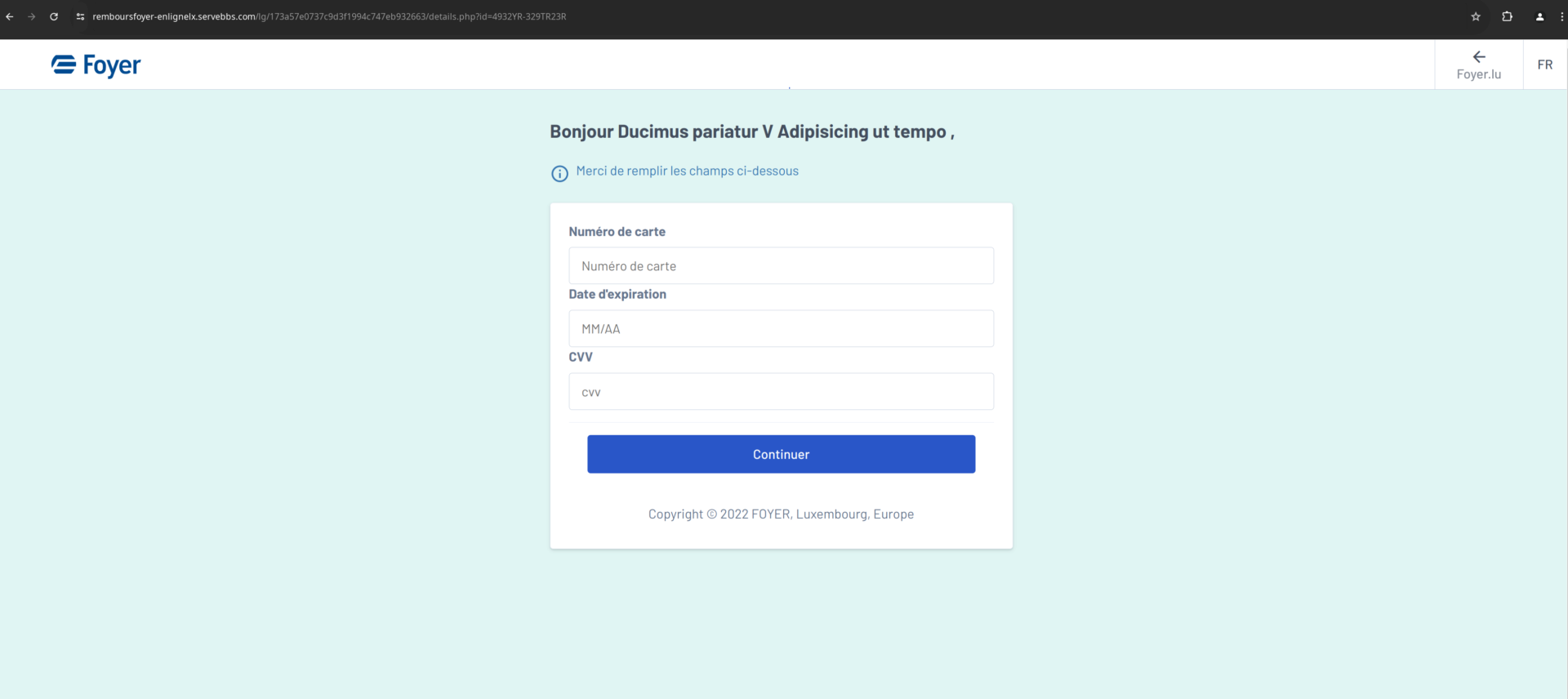
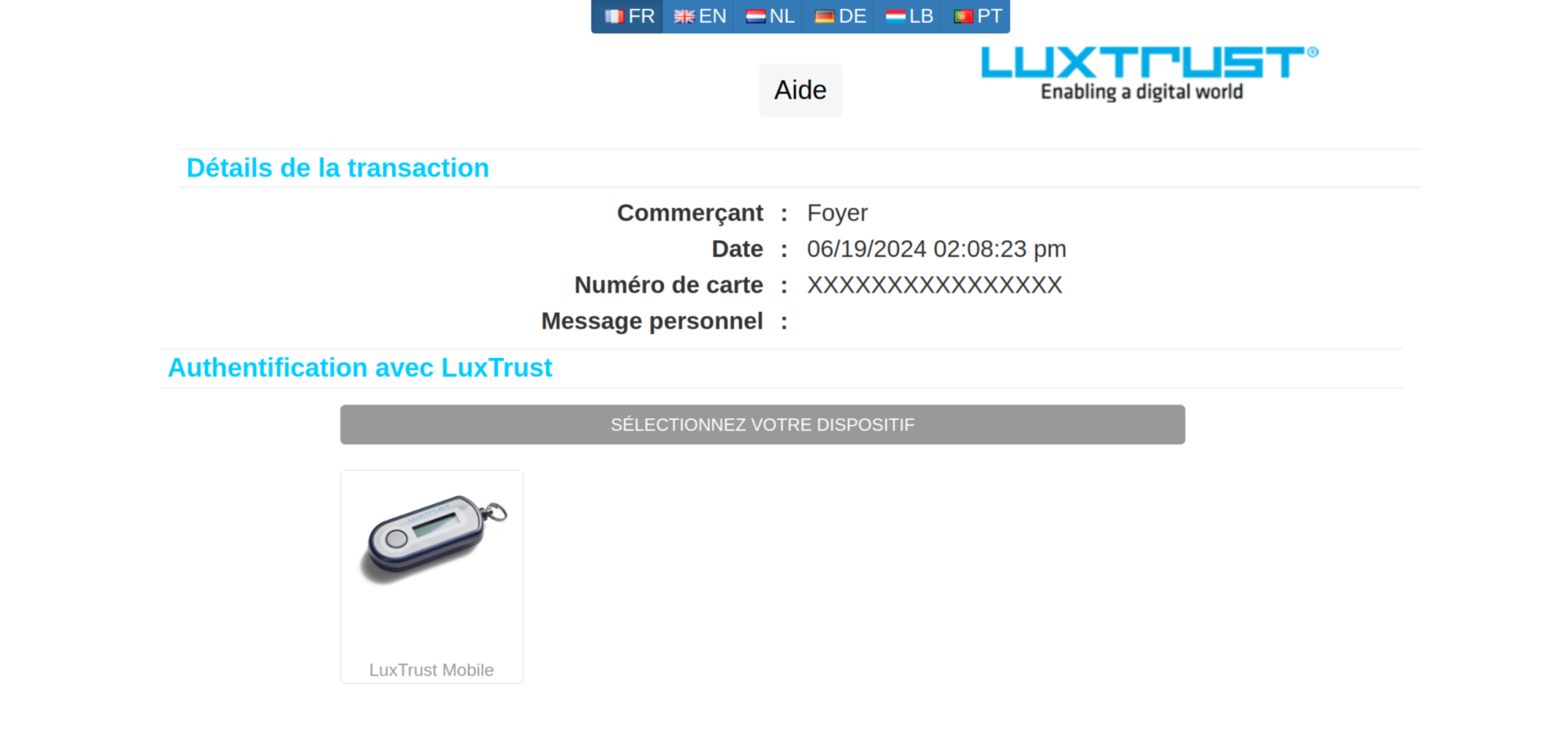
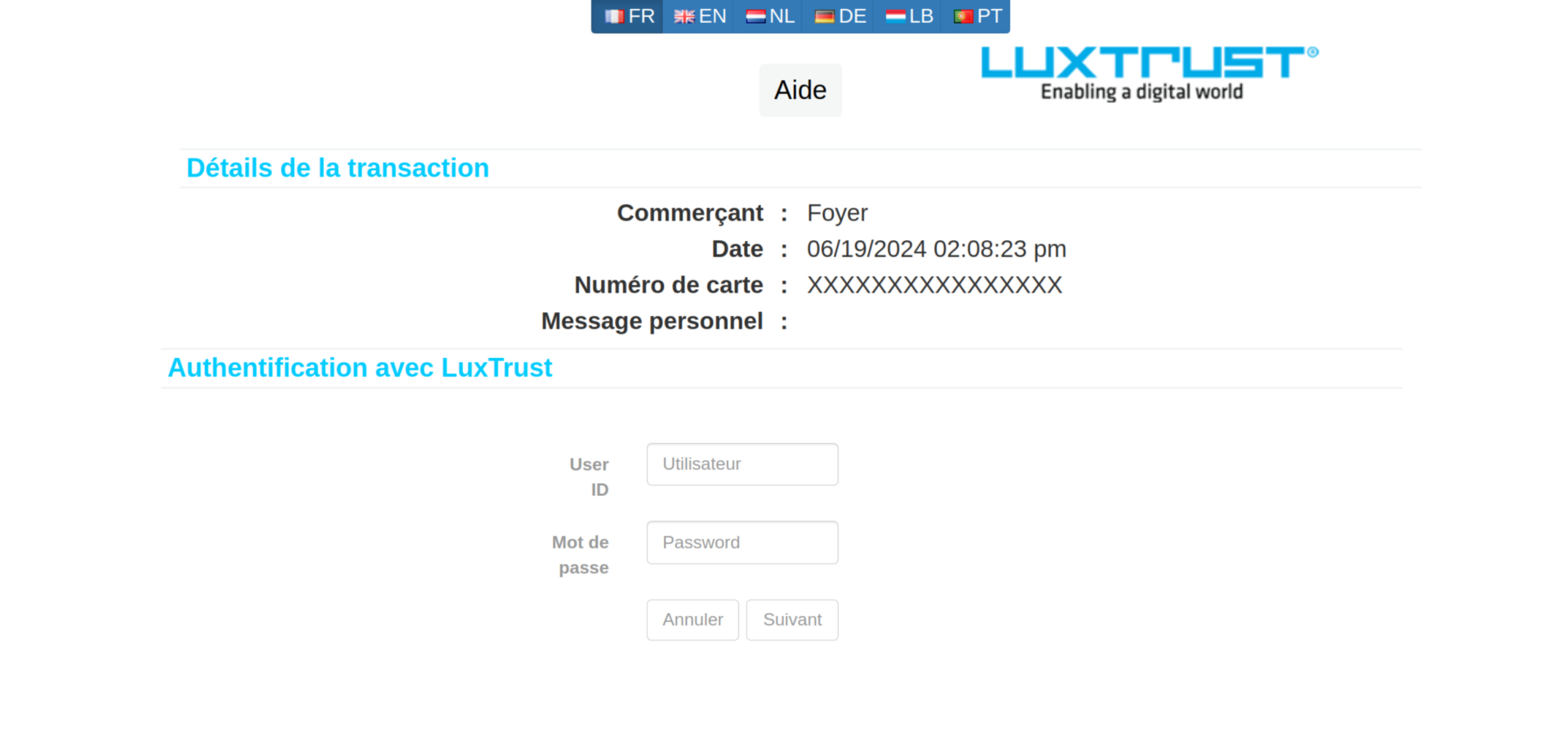
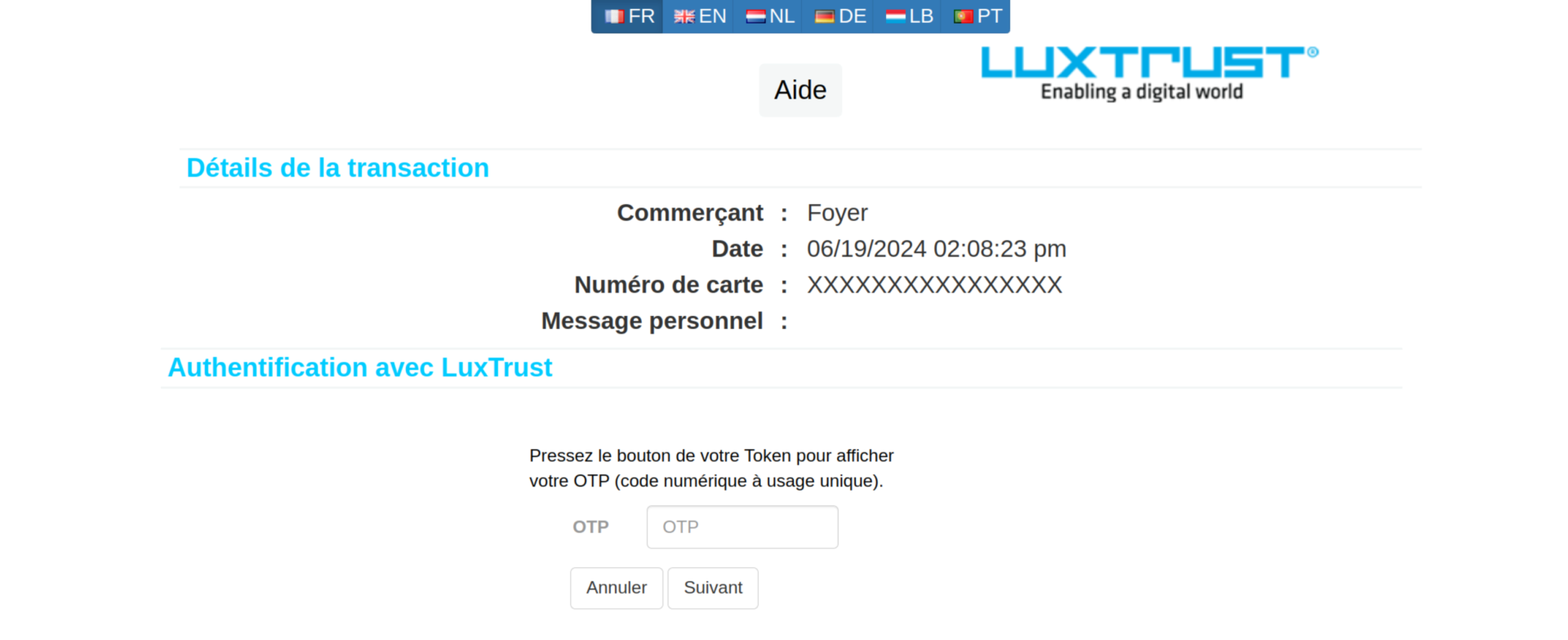
This link then redirects the victim to a page where they are first asked to enter personal data and then, in a second step, credit card details. A single authentication method can then be selected: LuxTrust Mobile. However, the text does not match the corresponding image, which shows a LuxTrust Token. The other options such as LuxTrust Token, Scan, SmartCard, Signing Stick and eID Luxembourgeoise are missing from this phishing. Finally the victim is prompted to enter the respective authentication details (User ID, Password, OTP token).
All the steps described above have taken place on pages under the malicious domain ‘remboursfoyer-enlignelx.servebbs.com’ .
Example