Explanation
The goal of this phishing campaign is to steal Microsoft 365 credentials. The distribution happens via email; according to our knowledge mainly by compromised accounts.
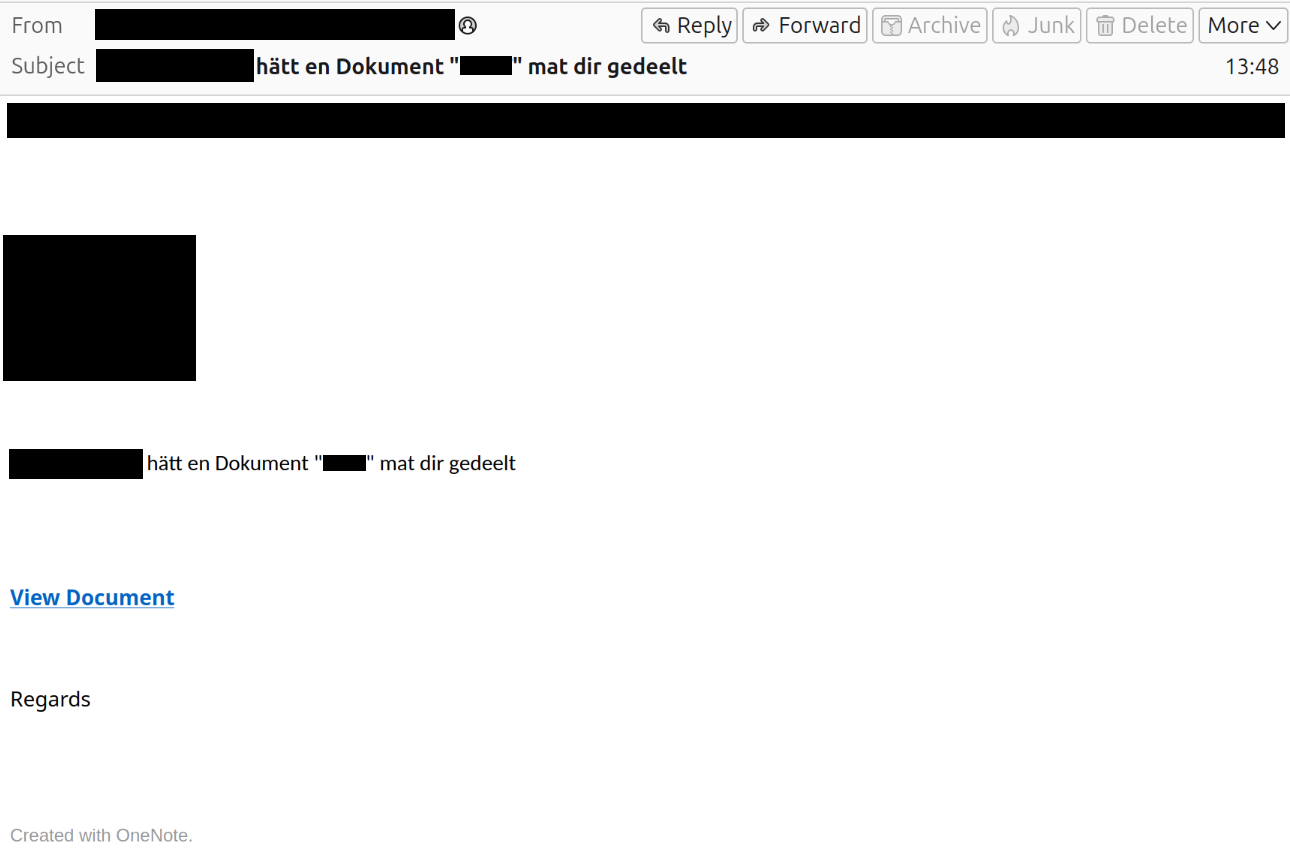
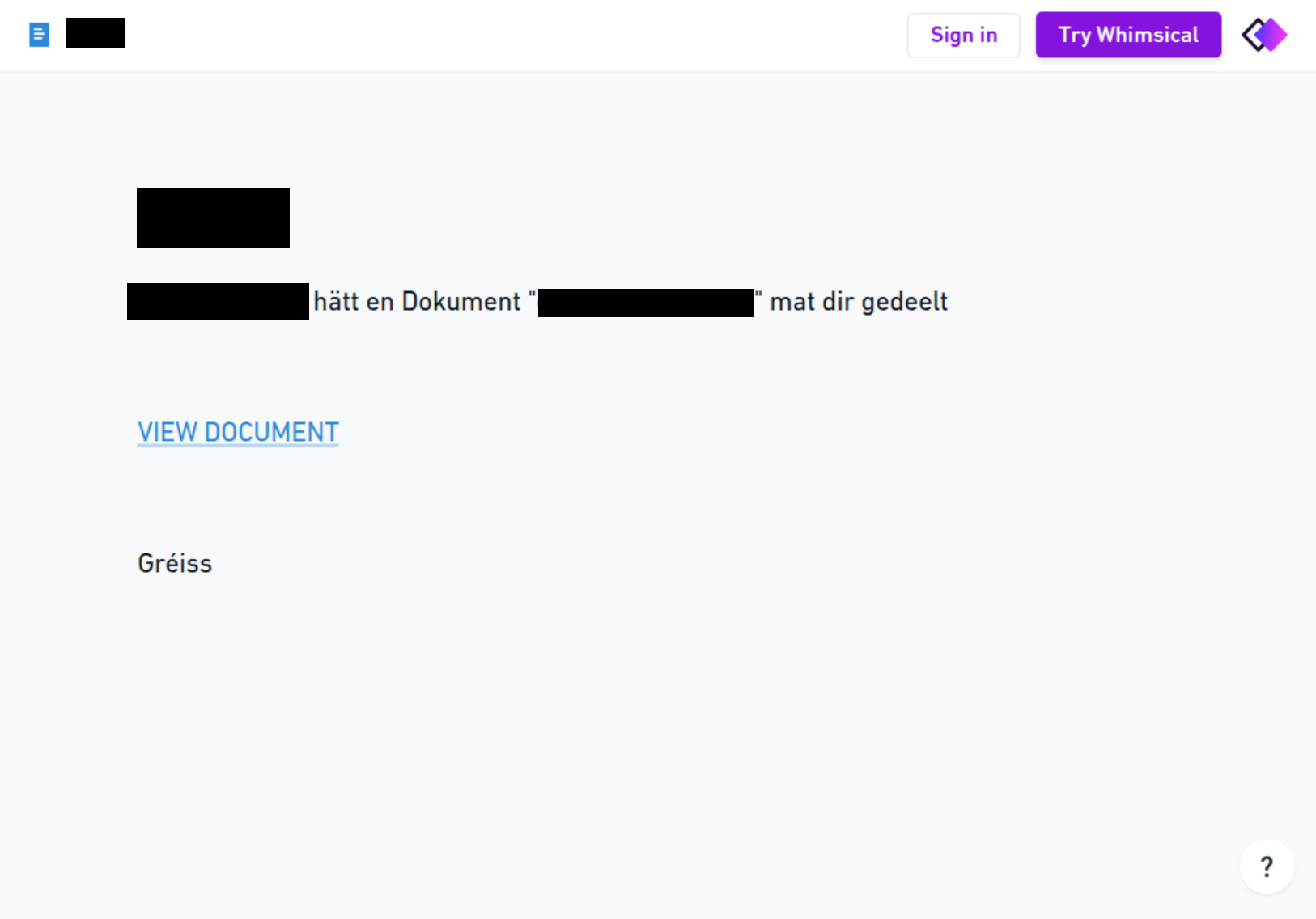
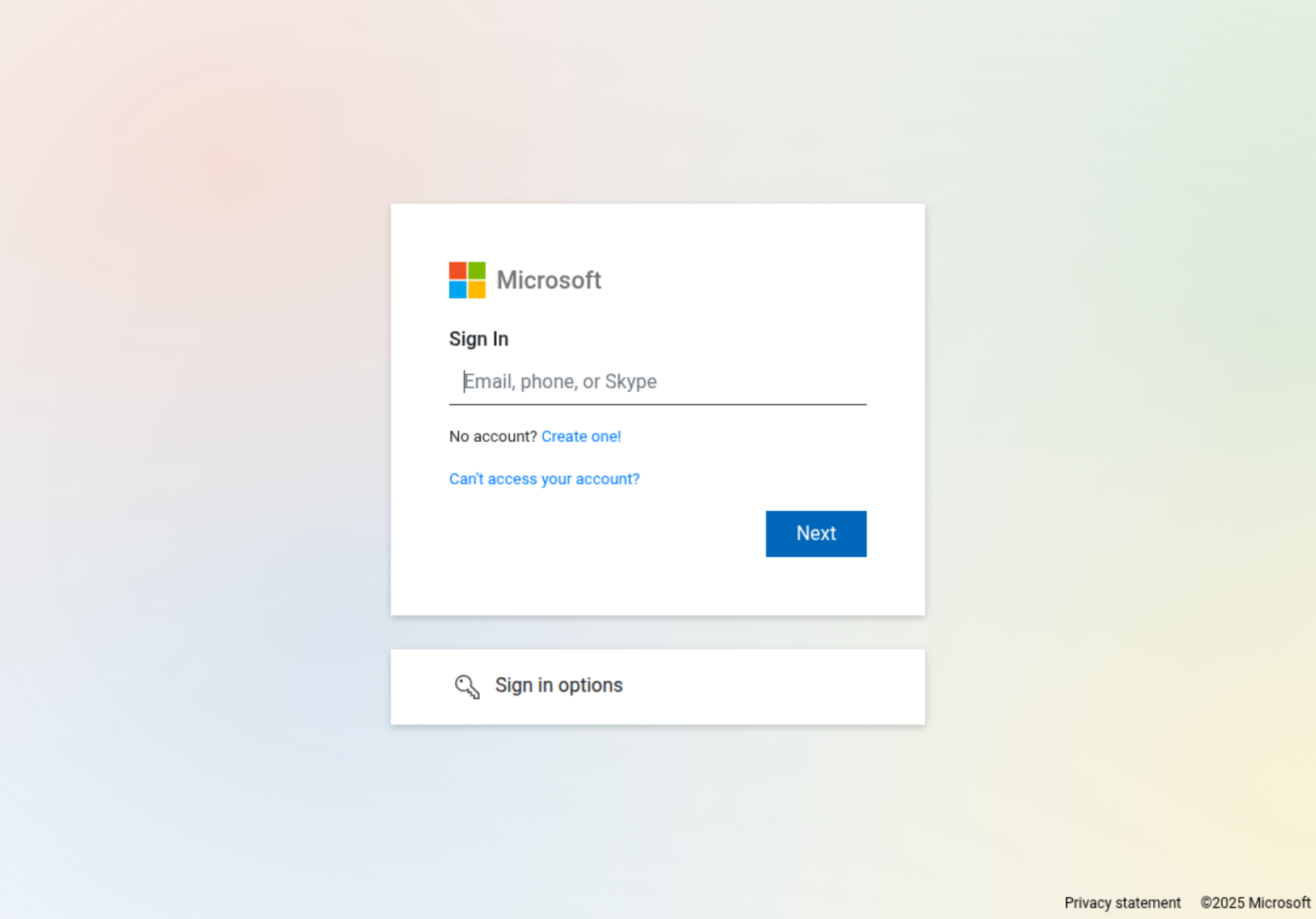
In the rather plainly written email it is claimed that another person has shared a document. Hereby it is possible that the language changes, even within the message. However, if the user clicks on “View Document” they are redirected to a malicious website. At that point, the user is prompted again to click “VIEW DOCUMENT” to supposedly access the file. Clicking on that link redirects the user then to a fake Microsoft 365 login page.
Note: The overall approach and appearance of the individual pages may deviate slightly from the previously described.
The following domains were observed in the context of this phishing campaign:
- *.bard.it[.]com
- whimsical[.]com
Example