Explanation
The goal of this phishing campaign is to steal Microsoft 365 credentials. The distribution happens via email; according to our knowledge mainly by compromised accounts.
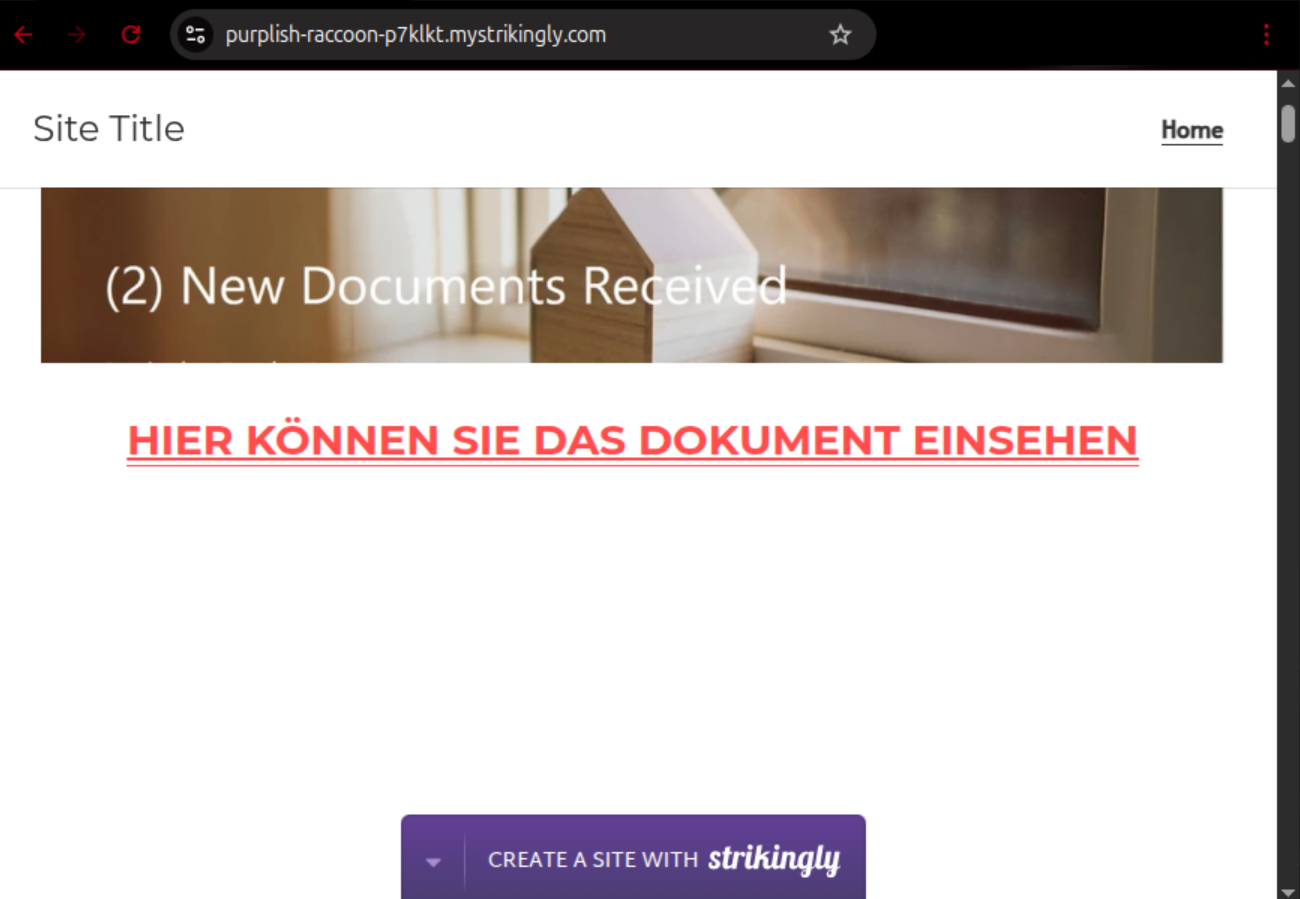
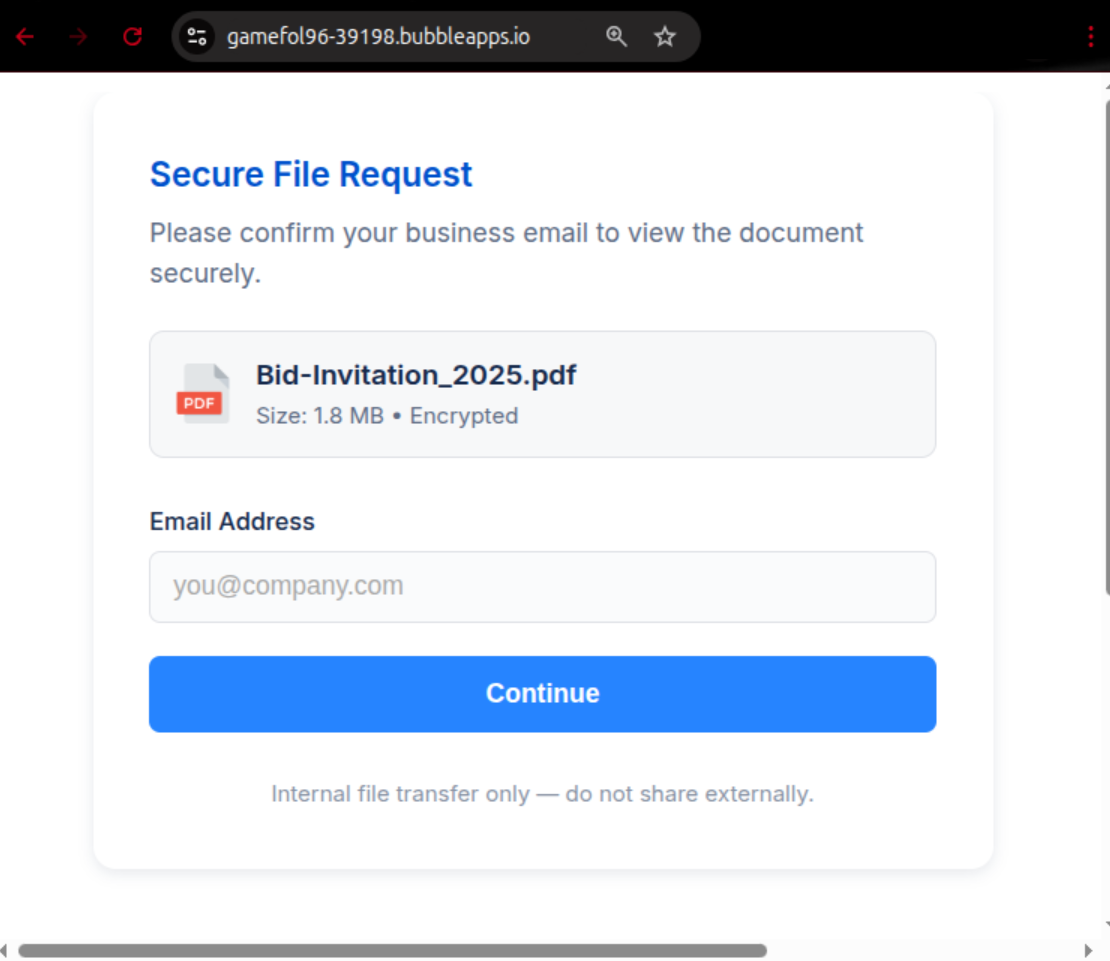
In the message itself, there is an embedded image, which contains a blurry view of a supposedly relevant document. By clicking on that image, the respective PDF documents should allegedly be displayed. In reality, the user is redirected to a malicious website, for which there are several variants.
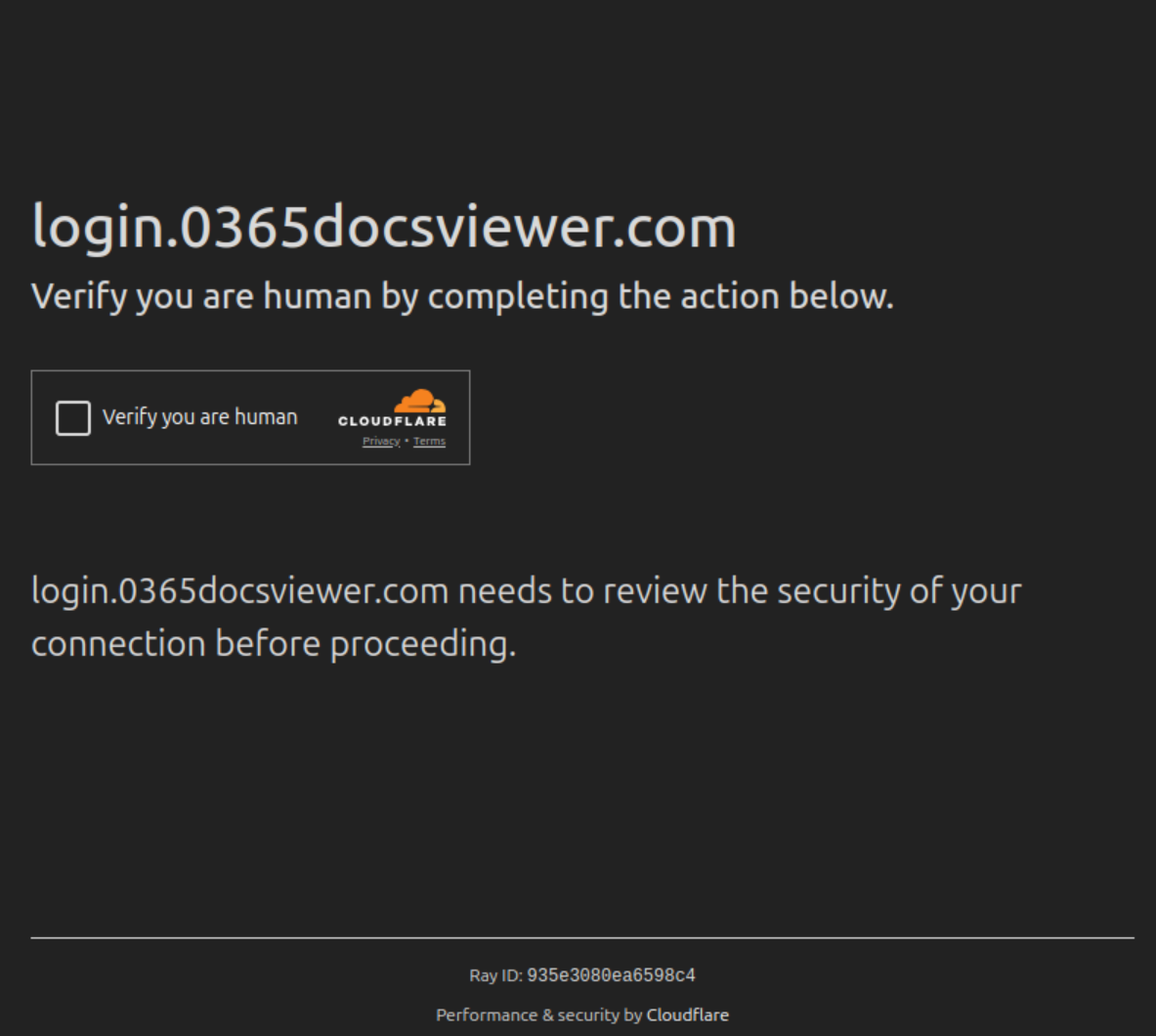
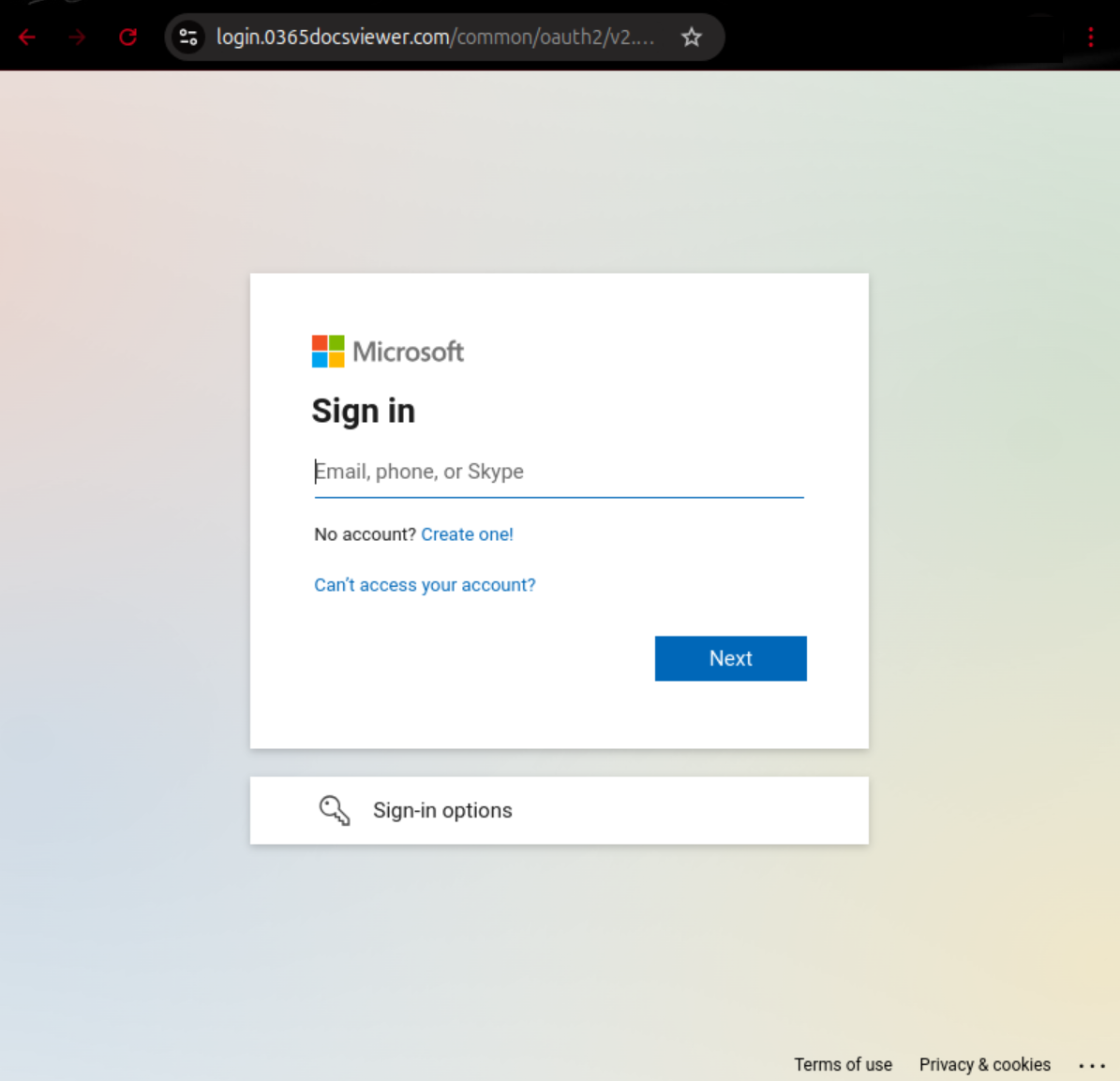
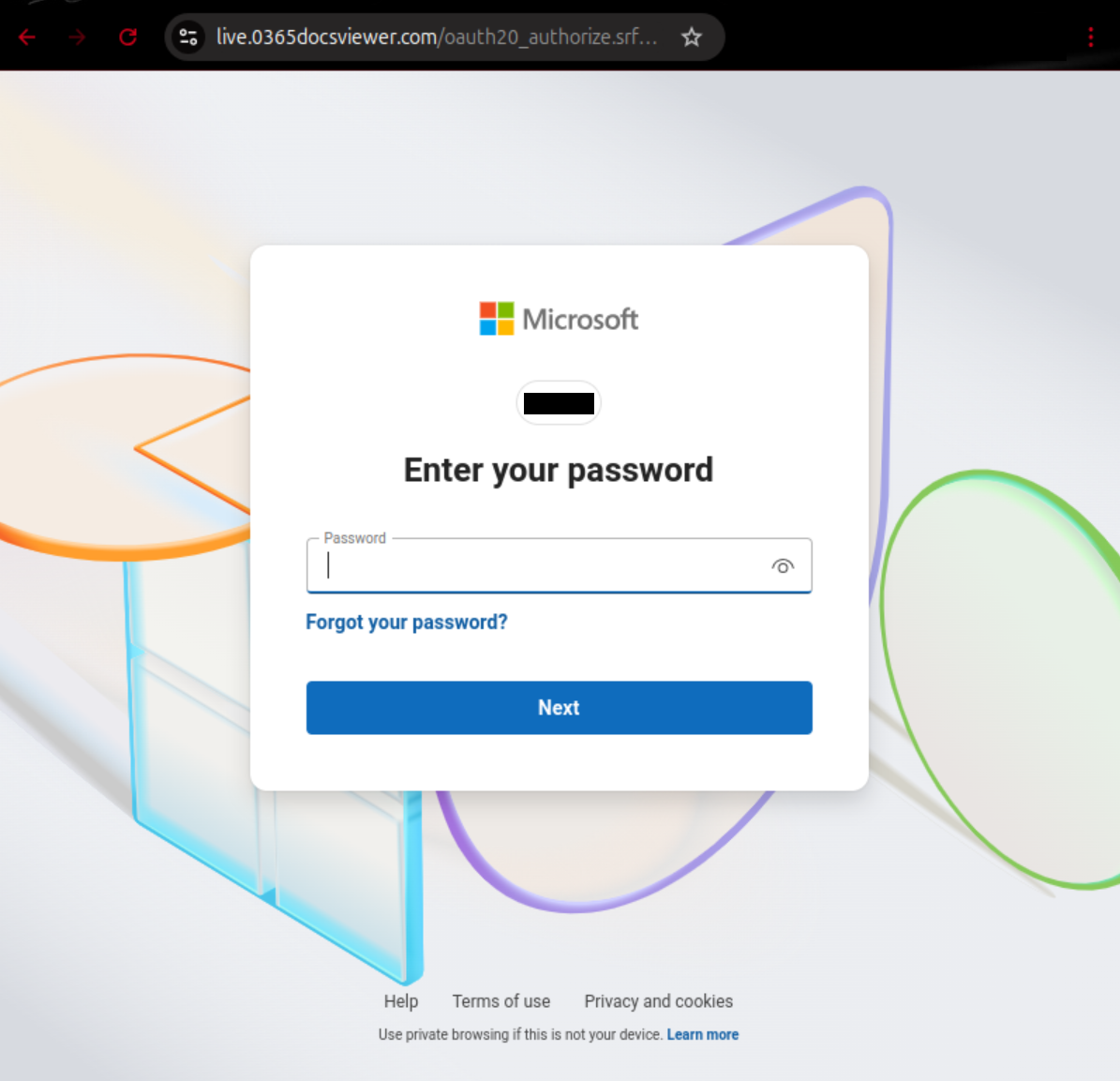
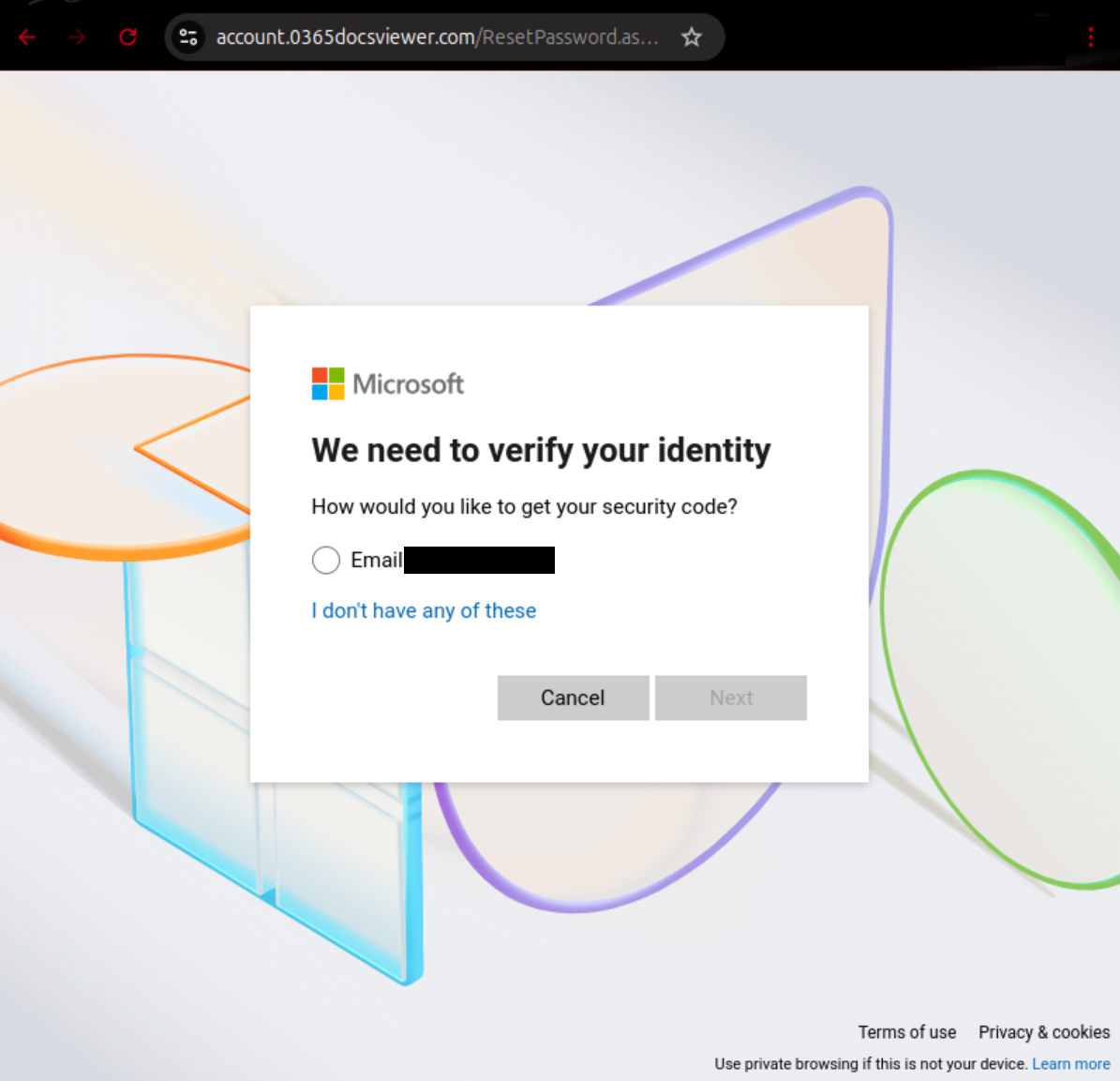
If one clicks on the URL on that page, one gets redirected to a page under another domain, where Cloudflare’s human verification-step must be carried out first. Next, after a supposed sign-in initiation process, the user is asked to enter their username. Here, the phone number or Skype account linked to the Microsoft account can also be used. Subsequently, the password is requested. If one clicks on “Forgot your password?”, the email address associated with the previously entered account will be extracted from Microsoft and displayed. In this case, a password reset could indeed be carried out; however, the attacker can intercept the data in the process.
Note: The overall approach and appearance of the individual pages may deviate slightly from the previously described.
The following malicious domains were observed in the context of this phishing campaign:
- *.0365docsviewer[.]com
- *.notionshare365[.]com
- *.pdfhubo365[.]com
- *.sharep0int365[.]com
- bolder-machine-9ae.notion[.]site
- gamefol96-39198.bubbleapps[.]io
- honest-falcon-p5wdmk.mystrikingly[.]com
- lavender-carnation-pb9ctx.mystrikingly[.]com
- maze-sneeze-b7e.notion[.]site
- officefilescloudstoragesystem[.]com
- purplish-raccoon-p7klkt.mystrikingly[.]com
- witty-stem-46c.notion[.]site
Example