Explanation
Threat actors are using a fake Metamask cryptocurrency wallet theme to trick potential victims into submitting their recovery pass-phrases.
The risk is that recovery pass-phrases can be used to access a Metamask account, without having a username nor password. The Metamask cryptocurrency wallet supports transactions of several cryptocurrency types. Hence, this attack is generic and does not target a specific cryptocurrency.
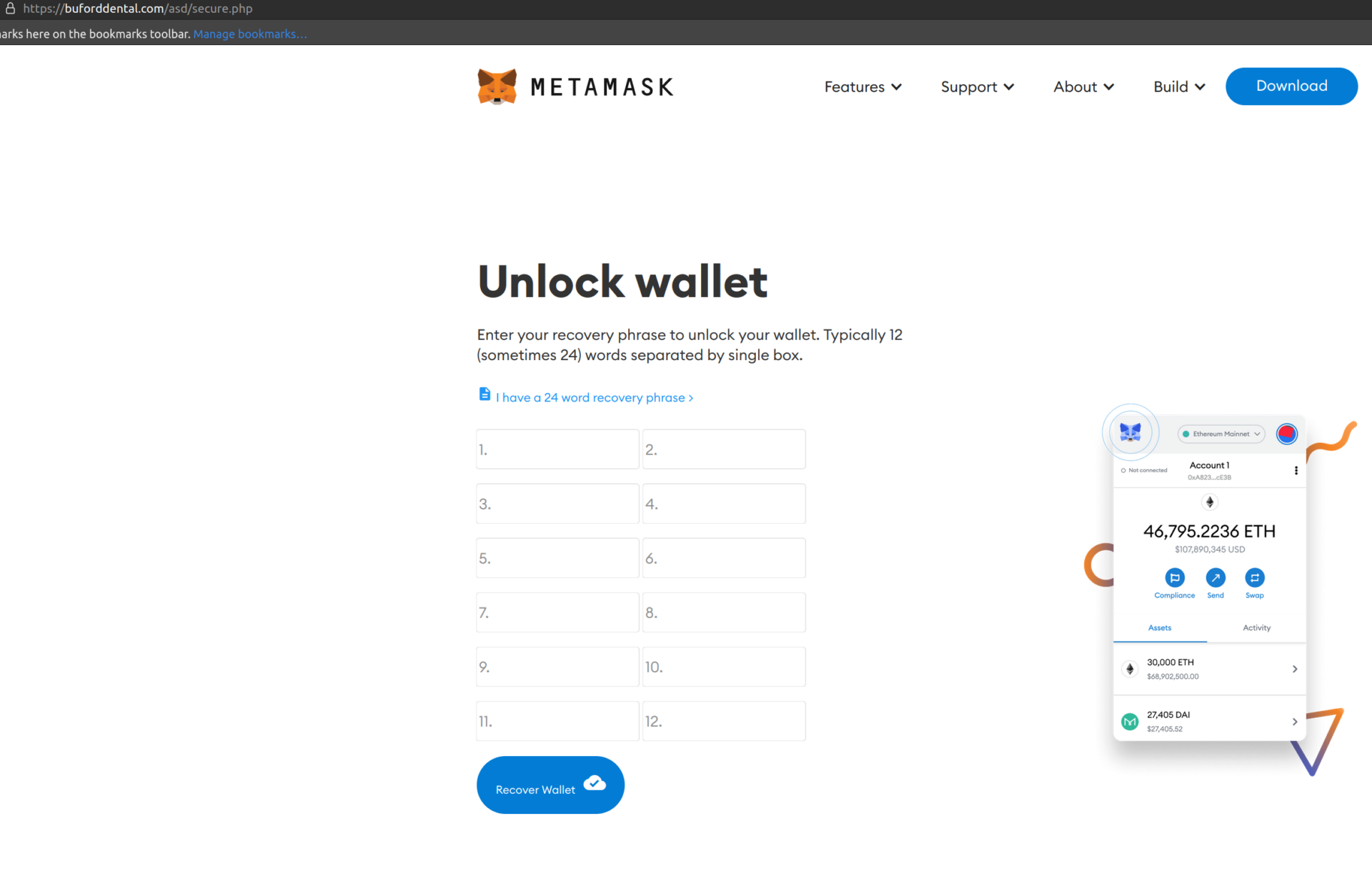
In the phishing e-mail, we can see that the e-mail address of the sender, admin@worldmedicalalliance[.]com, is not in relation with Metamask. When clicking on the “Verify your wallet” link, a fake Metamask page with a recovery pass-phrase form is presented. Even if the page is well designed, the domain in the URL, buforddental[.]com, is not from Metamask.
All the others buttons in the phishing web page, redirect to the official Metamask website. For instance, when clicking on the “Download” button a redirection to https://metamask.io/downloads takes place.
Example