Explanation
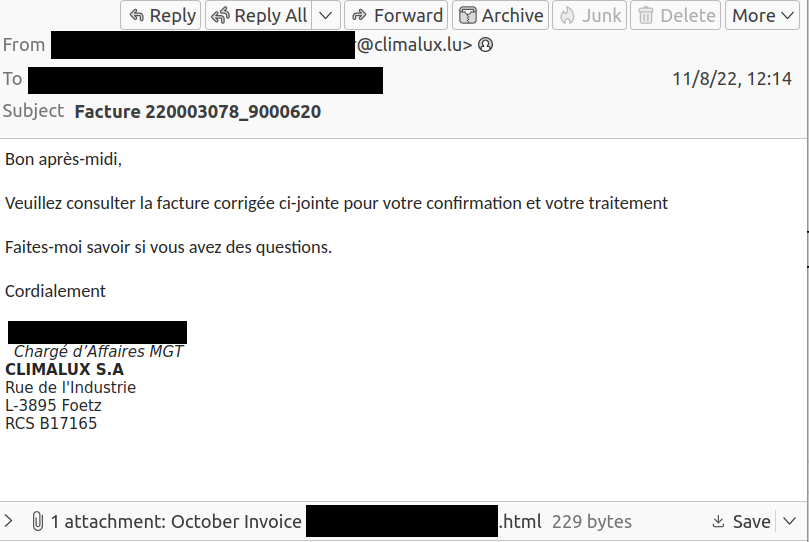
Threat actors are impersonating a Luxembourgish company to collect Office 365 credentials.
The attack starts with a spoofed e-mail that tells the victim that they have a corrected invoice that needs to be reviewed.
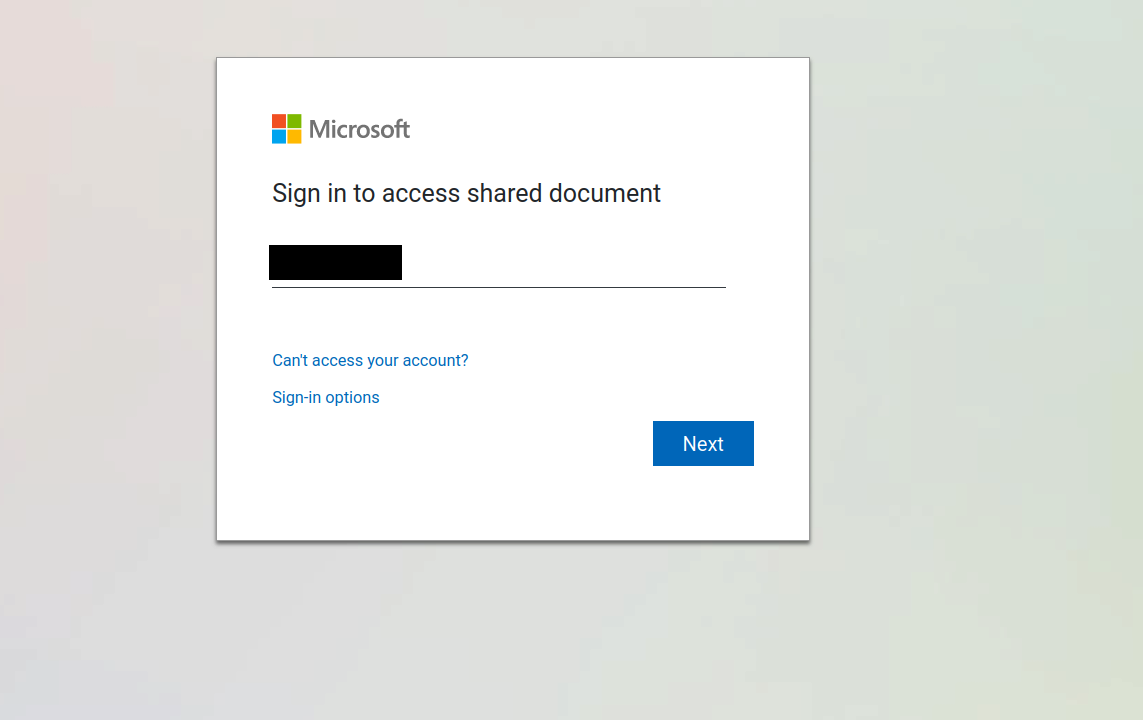
The e-mail text leads the victim to open the attachment, which redirects to the phishing landing page shown in a web browser.
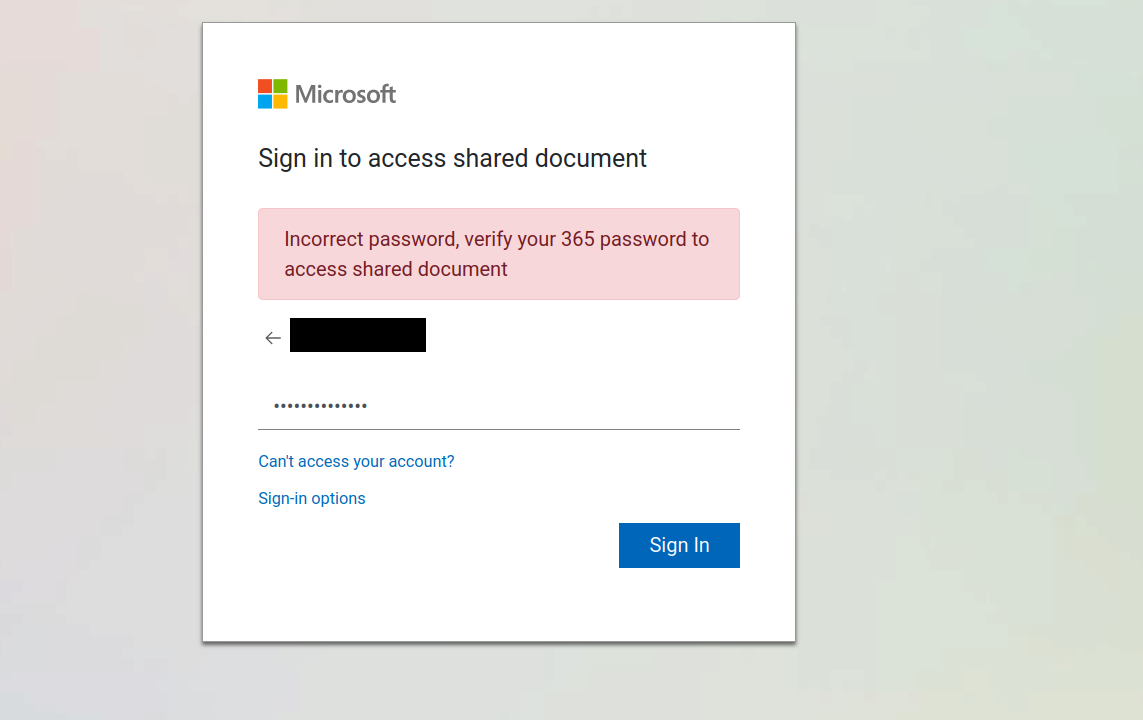
When the credentials are entered, an error message shows up and no further action is taken.
No invoice file is ever downloaded.
Please note that the spoofed e-mail does not originate from climalux.lu.
Example