Explanation
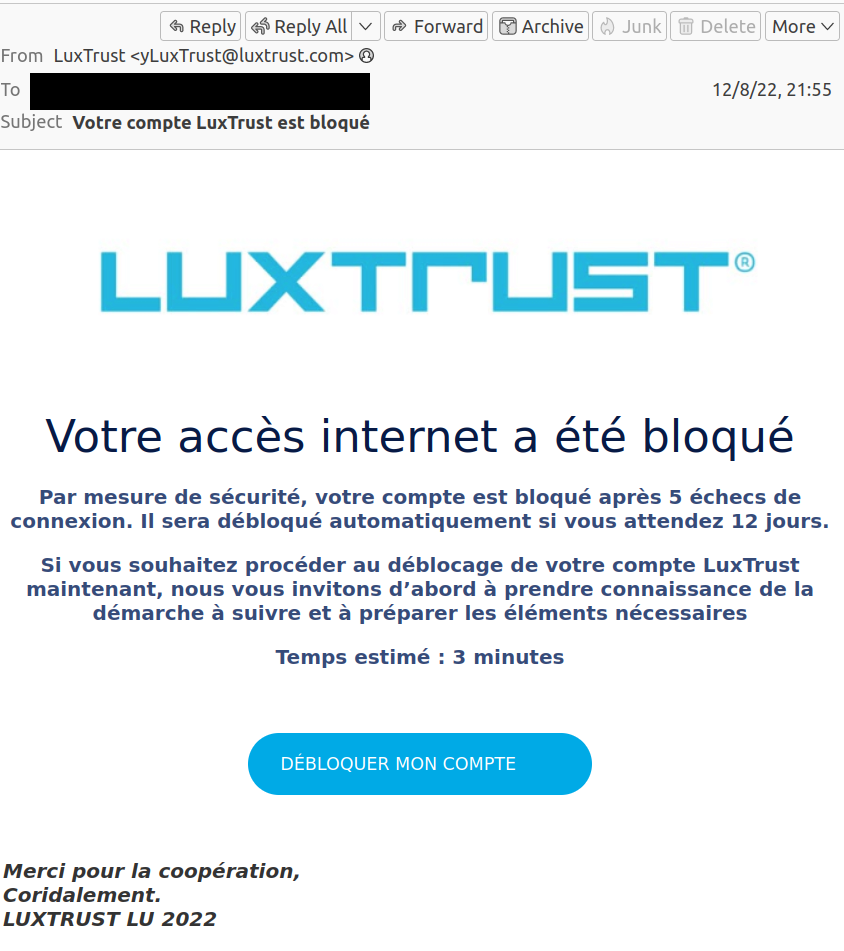
Threat actors are trying to collect credit card information, Luxtrust credentials and OTP token.
The phishing mail leads the user to believe that their LuxTrust account access has been blocked, and by clicking on the link the user is redirected to the phishing landing page.
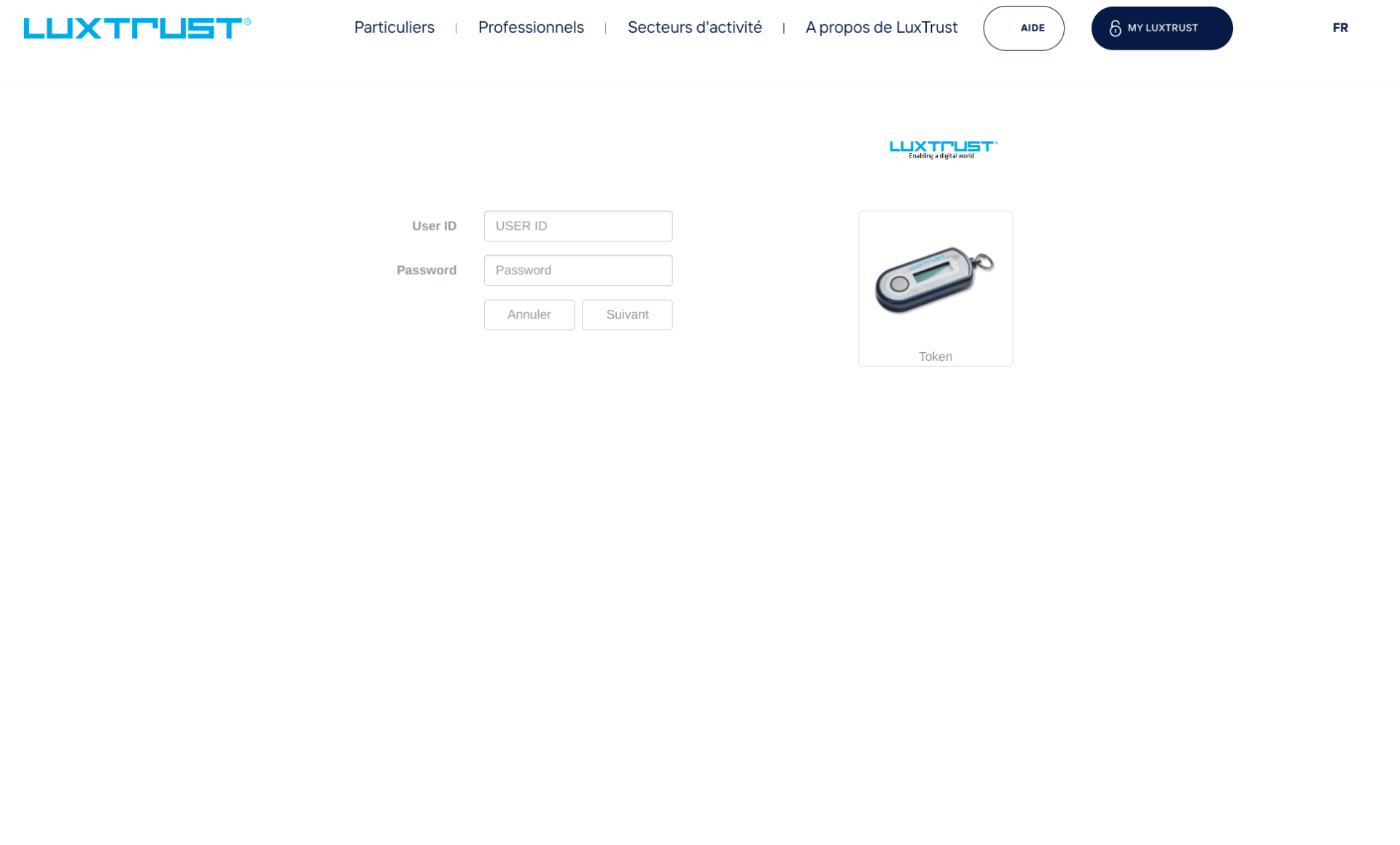
On the first landing page, the victim has to choose a bank. Once the bank is selected, the web page redirects the victim to a form where the goal is to collect Luxtrust token one-time-passwords and credentials.
Note that the e-mail and the landing page are not associated with LuxTrust. Although the e-mail has a from @luxtrust.com, it was not sent from an official LuxTrust server (spoofed).
Example