Explanation
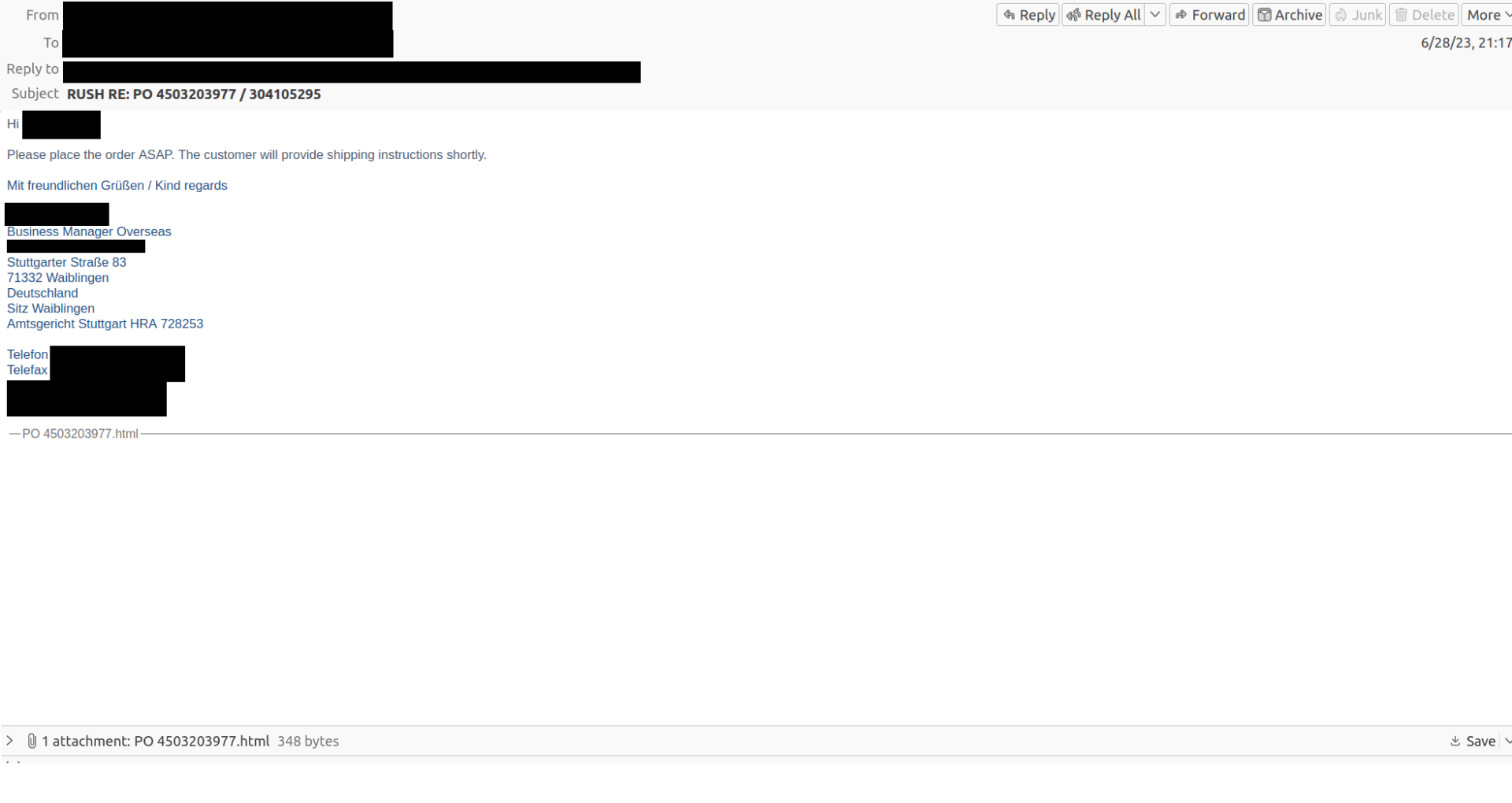
Threat actors are using compromised accounts to collect personal information and credit card information.
By using compromised accounts, the e-mail seems legitimate at first glance as it seems to originate from a known and trusted source. In reality, however, it is malicious.
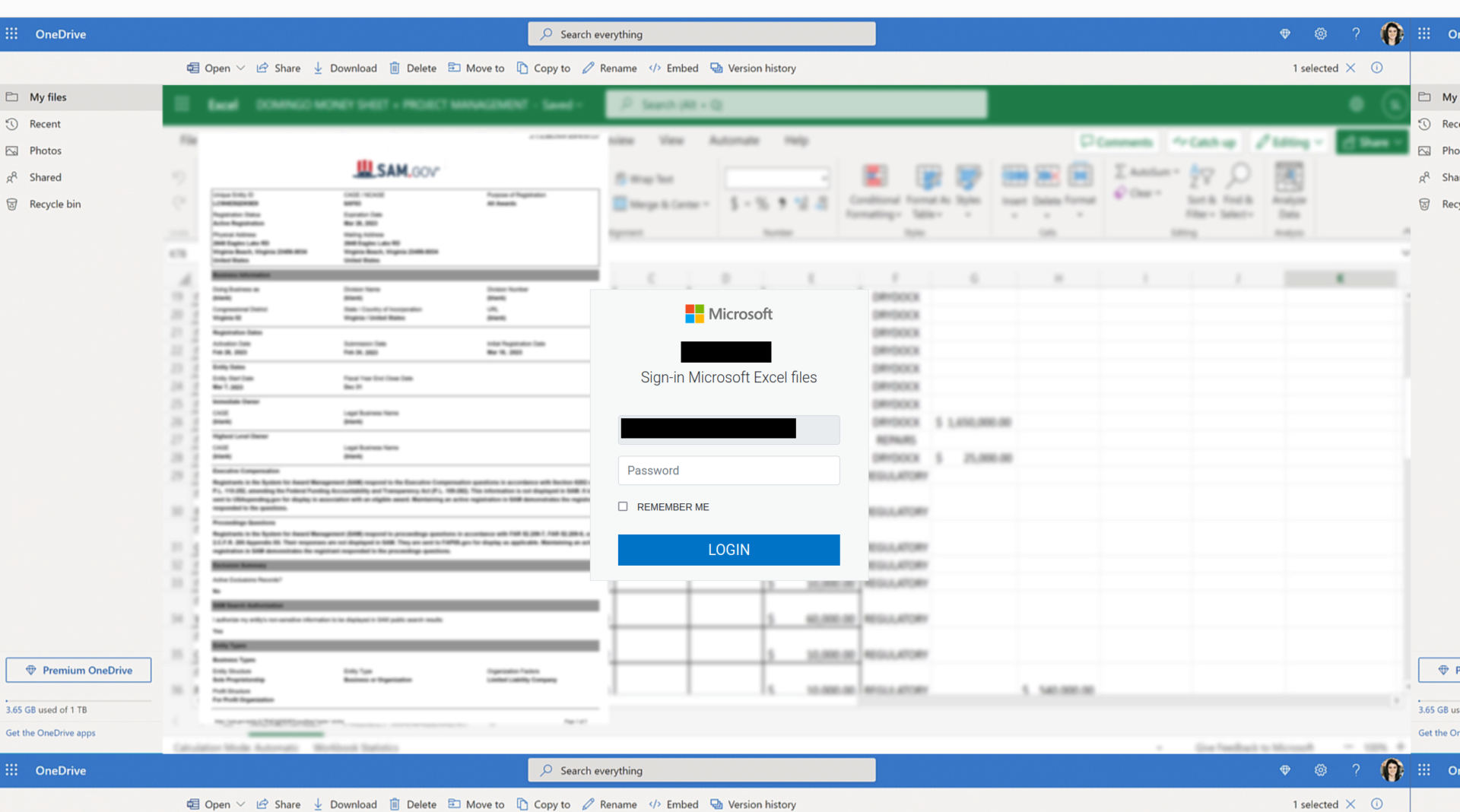
The phishing mail leads the user to believe that they need to place an order. By opening the attachment, a phishing form with a fake Microsoft Excel document in the background is shown to collect the Microsoft 365 credentials.
Example